Use the rule editor to define a rule’s settings.
Overview
Whenever you define or edit a rule, you will use the Rule Editor to make the necessary configurations. The rule editor opens any time you: Add a new rule (template or custom), Edit an existing rule, or Duplicate an existing rule.
The rule editor is divided into four different sections of configurations:
-
Name and Description (Required)
-
Applications, Activity Type, and Alert Threshold (Required)
-
Criteria (Required)
-
Response (Optional)
When all four sections of the rule editor are configured properly, click SAVE to deploy the policy.
Only items relevant to your license type will be available in rule configurations.
If you are creating a custom rule, you must configure each section in order to advance through the rule editor. If you are using a rule template or exiting an existing rule, you can navigate to any section to make edits because each section is already configured.
This help page provides detailed instructions on how to configure all sections in the rule editor.
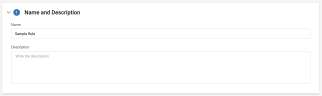
1. Name and Description
Rule Name
-
Enter the rule's Name in the respective text field.
-
The Name should be unique and allow Cloud DLP users to quickly identify and differentiate the rule from other existing rules.
Rule Description
-
Enter a Description of the rule in the respective text field.
-
Use the description to provide additional clarification on the rule’s permissions and/or use case.
Click Next to move to the next section.
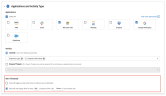
2. Applications, Activity Type and Alert Threshold
In this section, define which Applications the rule will monitor and the specific Activity type(s) it will detect. You can optionally set an Alert Threshold to only receive alerts when an aggregated number of rule matches occur.
Applications
A single rule can trigger alerts on activities coming from multiple cloud applications. This eliminates the need to add separate rules per individual app.
-
Define which Applications the rule will monitor by clicking an app's checkboxes
-
The rule will only monitor selected connected cloud apps
Only your connected cloud applications are available for selection. If a cloud application you want to monitor is not shown, you can Administration > Integrations > Cloud Applications page using the “Add more applications” link.
Define the Activity Type
A rule can either monitor specified user activities or search an event for known threats. A Known Threat is a pre-defined activity, sequence or set of indicators which often indicates suspicious behavior. The more activities you select in a rule, the broader the scope and the more complex it can be to administer the rule, apply remediations, modify users, etc.
Consider creating narrow rules for specific use cases that map only to a small number of activities. This will help you maintain the rules as they fire in your environment.
-
Select either the Activity or Known Threats radio button.
-
A dropdown menu of related options will display.
-
Select item(s) from the dropdown menu.
-
The rule will monitor your selected items.
Only activities and threats relevant to the rule category and selected apps will display.
You cannot select Activities when Known Threats are defined (and vice versa).
Define the Alert Threshold (Optional)
By default, a rule will trigger an alert each time a matching event occurs.
You can create rule that triggers only when a high volume of matching activities in the rule’s specified apps are performed by a single user in a defined time period.
Example use case: Create a rule that detects when a user is performing massive file downloads or deletions in a short time period.
The intention for a volume rule is to detect instances of atypical user behavior. If you want to remediate on single user activities, you will need to define an additional rule with remediation actions.
If the total number of matching activities exceeds the total number defined in the rule, only one alert will fire during the chosen timeframe.
1. Define the alert threshold for the rule.
-
Choose the number of instances/events (Minimum 2, Maximum 5000)
-
Choose the time period (Minimum 5 minutes, Maximum of 24 hours)
When a rule with a defined alert threshold is created or updated, the system starts counting alerts after the rule is saved.
To view all associated activity matches (instances) and/or resources that caused the rule to trigger, we recommend the following: In Analytics, open the Alert’s Side Panel > Summary Tab > Origin Card > and click the Open Timeline link. This will show a list of all events for that user in the time period.
Click Next to move to the next section.
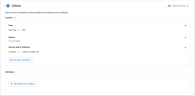
3. Criteria
This section provides information on using the rule editor when in Simple mode. If you need to create conditions using advanced AND/OR logic, you can switch the Criteria section into Advanced Mode .
Define what criteria is used by the rule to determine if it will match with an event.
Context conditions are required and you must specify all three: User, Device, and Source and IP Address.
Attributes are not-required, these are additional conditions you can use to further limit a rule’s scope.
You can select the following Attributes per rule type:
-
Access and App Governance: Authentication App Name, Findings Type, Login Status
-
Data: Collaborators (Event), Data Classification, Share Level, File Extension, File Insights, File Paths, File Size, File Types, Google Badge Labels, Malicious Content, MIP Label, Object Type, User Priviliges
-
Configuration and Security Positive: Activity Type, Insights, Risk Level, User Privileges
How to Define Criteria - General Steps
Hover your cursor over any criteria item to access its edit controls, then define match criteria using the intuitive Add, Edit, Save, and Delete controls provided.
For each criteria item, you must specify "IS" or "IS NOT."
Click the checkmark to save a defined criteria item.
A rule will only fire when there is a match in each required context condition and each defined attribute. Only ONE matching condition within a specified Context field and Attribute is needed for the system to determine the rule is a match.
Context
The Context sub section lists the three mandatory fields that must be defining in order for a rule to be valid: Users, Device, and Source and IP Address.
When adding a new rule from scratch, each Context field is configured to “match all” by default.
You can edit the Context fields or add additional conditions within a Context field to define a rule that is more limited in scope. Use the Add, Edit, and Delete Context controls for each listed Context field condition to make and save modifications.
For example, you can define an Access rule with the condition it will only match with individuals in the “Finance” user group who are also classified as a Very Attacked Person (VAP). To do this, define the following in the User section:
-
Group > IS > “Finance”
-
Click the + button to add a second User condition
-
User Type > IS > VAP
The rule will now only match with users who are both in the “Finance” group and who are VAPs.
NOTE: When 2 or more conditions are added to a Context field, the system needs to only find a match within ONE.
Because they are required settings, you cannot delete or remove a Context field or set its value to zero. If is no value is specified, the system reverts to the “match all” condition.
A rule only triggers when there is at least one match within ONE listed Context field condition.
Define Context - User
You can match all users (default setting) or include/exclude based on Users, Groups, and/or User Types.
-
Select one - User, Group, or User Type
-
Select operator - Is or Is Not
-
Select desired items from the drop down menu
-
Click the Checkmark icon to save your edits
Define Context - Device
You can match all devices or include/exclude specified User Agents.
-
Select one – Device Type
-
Select operator - Is or Is Not
-
Enter value to specify the User Agent string
-
Click the Checkmark icon to save your edits
Filter by complete or partial User Agent strings (case sensitive).
To filter by more than one User Agent, you can switch to Advanced Mode to specify OR conditions for User Agent.
Define Context - Source and IP Address
You can match all or include/exclude based on Locations, Networks, and/or IP Reputations.
Location: Lists of countries meaningful to your organization will display. (See Setup > Locations.)
Network: Lists of networks meaningful to your organization will display. (See Setup > Networks (CASB).)
IP Reputation: Proxy, VPN, Data Center Hosting, Tor.
-
Select one – Locations, Network, or IP Reputation
-
Select operator - Is or Is Not
-
Select desired items from the drop down menu
-
Click the Checkmark icon to save your edits
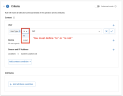
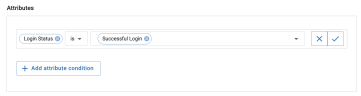
Attributes
The Attributes subsection (optional) allows you to add attribute conditions that further specialize a rule.
-
Add attribute conditions using the + Attribute condition button.
-
Hover over a saved condition to access controls for edit and delete.
-
Each attribute condition that you define further refines the rule.
-
Only attributes relevant to the rule you are defining are provided for selection.
-
A rule only triggers when there is at least one match within each specified attribute condition.
For example, if you are defining a Data rule that governs file sharing activity, you can make the rule only match when the event matches is for one of these available Share Level attributes conditions: Externally Owned, Public, External, All Domain, Internal, Private, Unknown.
Example: Using Rule Attributes
Here is an example of how you can tailor a rule to match with an even more limited use case:
If you are creating an Access rule that monitors logins, you can modify it so it only fires for logins made by users who are also Global/Super Admins.
To do this, define the following in the Criteria > Attributes section:
-
Click + Add attribute condition
-
User Type > IS > Global/Super Admin
The rule will now only match when the User is also a Global/Super Admin.
How Do Attributes Affect When a Rule Triggers?
A rule only triggers when all rule attributes that pertain to the specified connected cloud application are a match.
This is because a rule can reference one or more connected cloud applications, however, the attributes defined in a rule do not need to apply to all cloud applications covered by the rule.
To understand how the system determines if a rule will trigger, keep in mind:
-
The system will only evaluate rule attributes that pertain to a connected cloud application
-
If a rule attribute does not pertain to a connected cloud application, the system will ignore the attribute
For example: Consider an access rule that is configured for several applications, including Box. This access rule includes a "device: user agent" context condition. Since Box's public API security events do not include user agent information, the system will ignore the "device: user agent" attribute when evaluating Box events. Instead, Box login events will trigger the rule if they match with all context conditions/attributes that pertain to Box in the rule.
Add Attribute Conditions (Optional)
-
Click Add attribute condition
-
Select an item
-
Select operator - Is or Is Not
-
Select desired items from the drop down menu
-
Click the Checkmark icon to save your edits
Click Save to move to the next section.
4. Response
Define what happens if a rule triggers.
-
Alert Settings are required.
-
Optionally, you set the rule to perform automatic Remediation Actions and deliver email Notifications whenever the rule triggers.
Alert Settings
The Alert Settings subsection is where you define the types of alerts the system generates in the Analytics app when the rule fires. The Analytics apps provides comprehensive information for each event detected in your connected cloud app environments.
Customize rule alerts to aid your security analysts in conducting security investigations and incident triage.
Define Alert Severity
-
Select the Alert Severity: Critical, High, Medium, or Low.
Alerts for this rule will display as the selected severity in the Data Security & Posture app.
Define Advanced Alert Settings (Optional)
The advanced settings option allows you to enable/disable Alert Focus Mode.
When enabled, alerts are ONLY generated for events that introduce new violations. This allows your teams to focus on alerts that may pose a threat or indicate a security violation. Enabled is the recommended setting and all added rules have Alert Focus Mode enabled by default.
When disabled, the system generates alerts for all events, even if the event does not introduce a new violation.
How Alert Focus Mode operates differently for access alerts vs. data alerts
-
For access rules - system will alert only once within 15 minutes for exact rule matches
-
For data rules - system will alert only once within:
-
6 hours for content download activity exact rule matched
-
6 months for content update activity or content sharing activity exact rule matches
-
-
For mail message activity rules (Message Accessed, Message Soft Deleted, Message Hard Deleted) - system will alert only once within 1 hours for exact rule matches
-
Data | Content Sharing activity types to reduce duplicate and non-actionable alerts for repeated sharing events, improving signal quality and investigation efficiency.
Tags
You can assign one or more tags to a rule. A dropdown menu provides a list of available tags to choose from. Each rule template includes built-in tags that correspond to its associated risks or use cases. You can manage tags in Tag Management .
When an alert is generated the tags display in Explorations and Alerts views in the Data Security Workbench.
Remediation Actions
For some rules, the Remediations subsection allows you to specify if a rule should perform automatic remediations to help prevent, mitigate, or reverse a security or data violation if the rule triggers.
Automatic remediations can help reduce attacker dwell time because the protections you need are enforced at the time of the event.
Only remediation actions relevant to both the rule and connected cloud app you are defining will display for selection. “No Options ” means the rule does not support automatic remediations for the cloud app.
For example, an Access Rule that monitors for suspicious logins in your Office 365 environment can be configured to automatically perform some or all of the following remediation when the rule triggers:
-
Suspend User
-
Revoke Session
-
Force Password Change
Define Remediation Actions (Optional)
-
For each cloud application specified in the rule, click on the drop down menu.
-
Select all desired remediation actions.
Define MIP Labeling (for Office 365)
Some Data rules designed to monitor your Office 365 app will allow you to specify the MIP Label.
MIP labels are also referred to as sensitivity labels. Like Data Loss Prevention (DLP), sensitivity labels allow organizations to classify, track, and protect sensitive information. Organizations create and configure MIP labels in their Microsoft tenants.
For complete details this feature, visit the MIP Labels page.
Only MIP Labels configured in your Office 365 service will display for selection.
-
Click on the MIP Label drop down menu.
-
Select the desired MIP Label actions.
-
Enable or disable the “Overwrite existing MIP labels” feature.
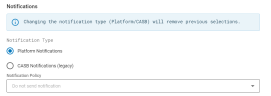
Notifications
The notifications subsection allows you to send notifications when a rule triggers.
Platform Notifications
Platform Notifications let you send email or webhook notifications when an alert is triggered.
Platform notifications are set up in Administration app (Integrations > Notification Policies). For details about how to set up a notification, see Customized Email Notifications for Rules.
For suggested Cloud DLP email templates, see Notification Policies for Cloud DLP\ATO Protection.
From the Notification Policy dropdown, select the notification you want to use.
With the platform notification policies you can:
-
Customize your notification with any alert field
-
Customize the text, its format and also include images
-
Set static or dynamic recipients
-
Send email or webhook notifications