Users Catalog
Users Catalog is a centralized user identity service that interfaces with directory services and provides enriched user information. Users Catalog consolidates user information from different sources and creates a single, unified identity for a user.
-
Users: Provides a list of users and risk information. From here, you can explore and filter users by their directory attributes, such as title, manager, location, users' groups, and risk levels and risk profiles.
-
Users Data: Provides details and insights about users.
-
Agent Integration with Users (Identity) Catalog: (For ITM / Endpoint DLP users) When the Agent is integrated with Users Catalog (Identity Catalog), the Agent receives the consolidated user information and uses it with detection and prevention rules.
-
ITD User Insights: Provides valuable context about the vulnerability of identities/users. This allows analysts to be proactive in blocking threats before the vulnerabilities can be leveraged for privilege escalation and lateral movement.
Users Catalog Information Sources
Depending on your entitlements, the information can be collected from the following sources:
-
Microsoft Entra ID (Microsoft Azure)
-
Google GSuite
-
OKTA Directory
Users and Groups are updated every 12 hours
Group Membership, Risk Profiles Memberships, Risk Scores are updated every 24 hours.
Information Collection
Information is collected via API ingestion or Cloud Connectors.
CASB customers do not have to create a Cloud Connector or Cloud Connector Data Realm. See Cloud Applications.
Collection via Cloud Connector
Cloud Connectors are accessed from the Administration app. (Administration > Integrations > Cloud Connector) Apps.
Microsoft Office 365, Google Workspace and Workday connectors are supported.
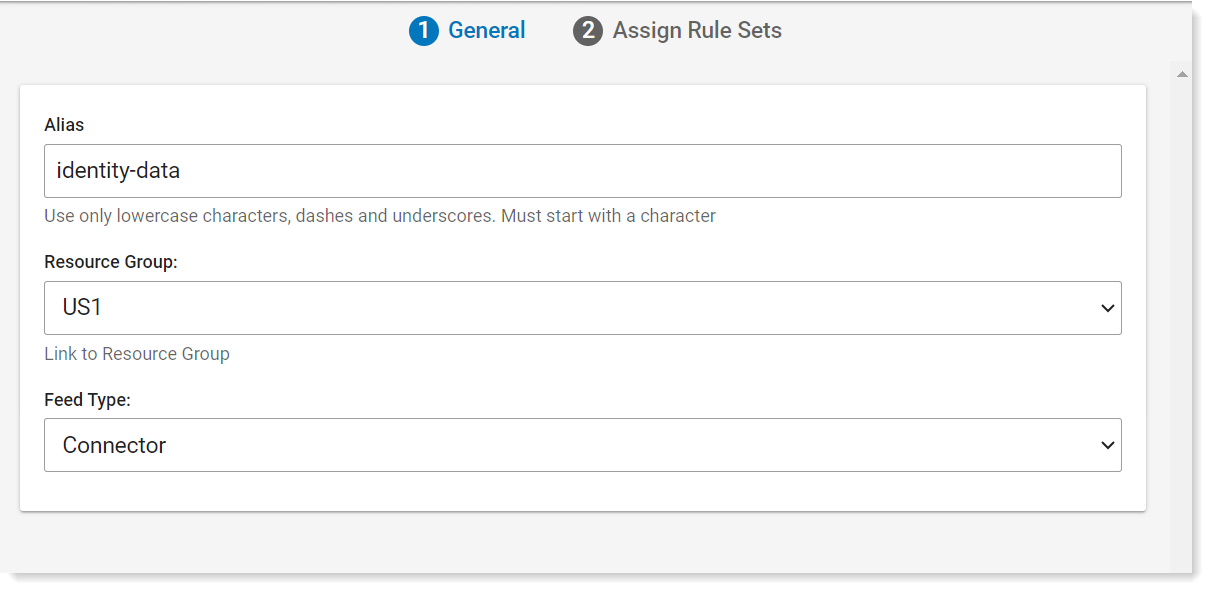
If you want to add a Cloud Connector, you create it as a Data Realm. (Administration > Integrations > Data Realm. Select Feed Type > Connector.) Select Connector as the Field Type
Creating A Cloud Connector
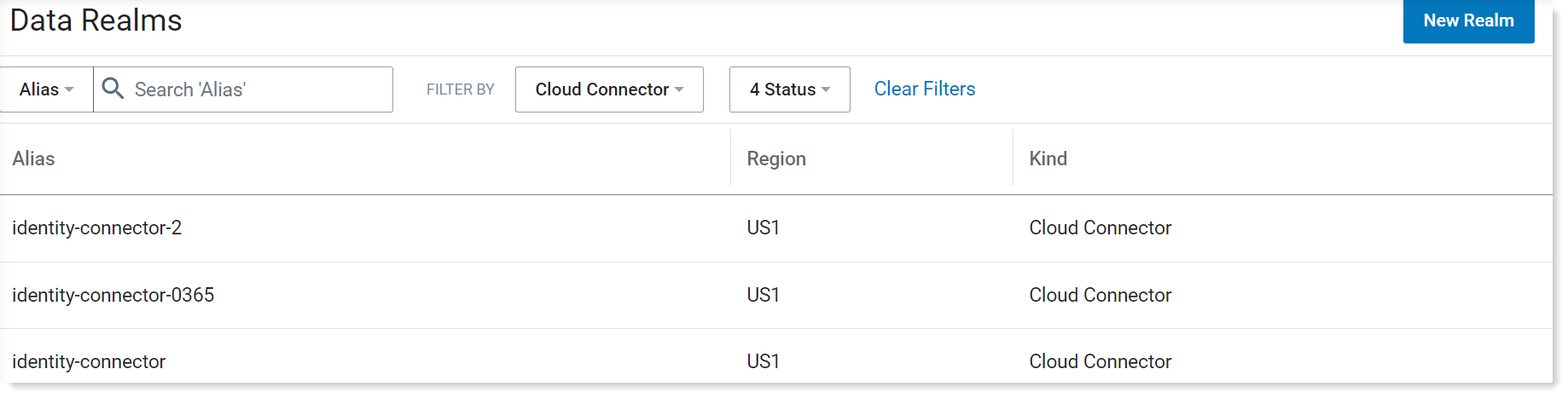
Cloud Connectors are created from the Data Realm Administration application. It takes several minutes for the Data realm to activate.
You can review the status of the Cloud Connector, from the Data Realms view. Status can be Active, Deleted, Error or Pending.
-
Select Integrations > Data Realm.
-
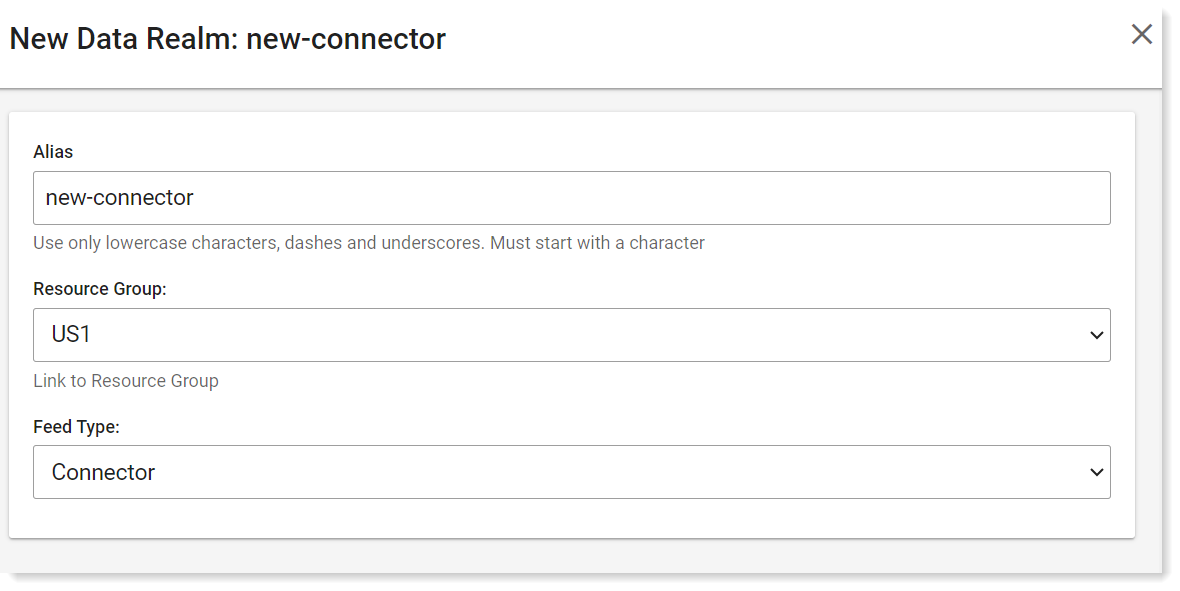
Click New Realm and select Connector as the Field Type.
-
In the Alias field, provide a name for the connector.
-
In the Resource Group field, select the relevant group.
-
In the Feed Type field, select Connector.
-
Click Save.
Connecting Cloud Connector to the Application
When the Cloud Connector is active, you can connect to the Service you want.
-
From Integrations, select Cloud Connector) Apps.
-
From the upper right of the screen, select the filter you want.
-
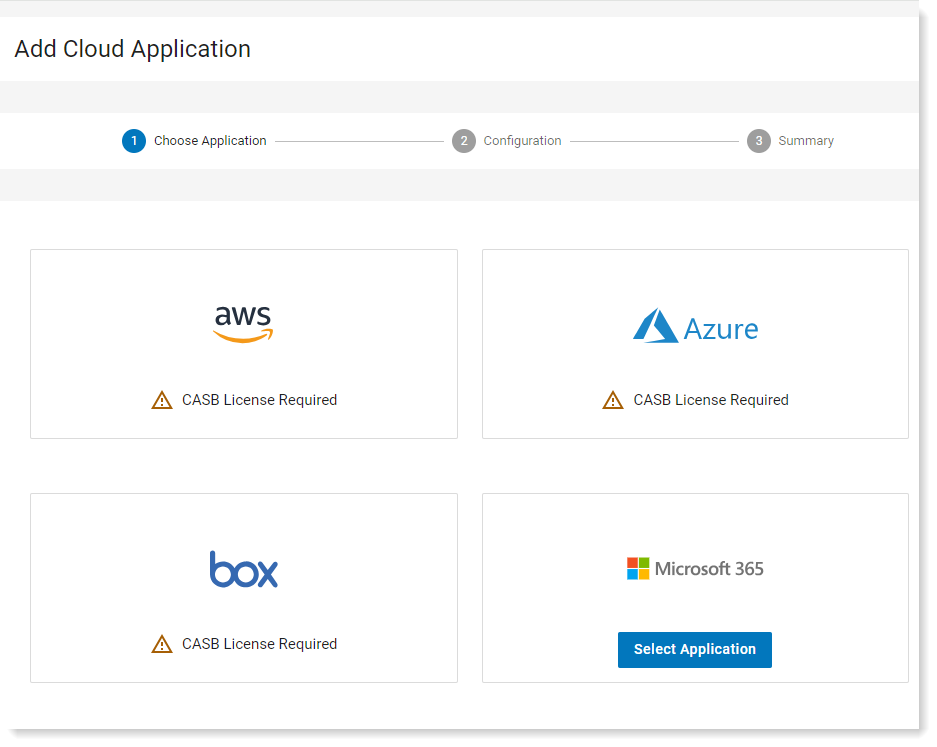
Click Add Application. The Application screen displays. Applications are available for your selection depending on your entitlements. Currently Microsoft 365 is available.
-
Click Select Application.
-
In the Choose Application tab, select the applications you want.
-
In the Configuration tab, select the Connection Type as Identity Only.
-
Click Connect.
You are redirected to the relevant application.
For Office 365
Prerequisites:
Create a Global Administrator or Privileged Role Administrator user.
-
Sign in with the dedicated admin account.
-
When prompted, accept the scope requirements.
-
You are returned to the Proofpoint console and a confirmation message appears.
-
You are now integrated with Microsoft 365
Collection via API Ingestion
For details about the API, see Proofpoint Developer Portal in Proofpoint Data Security & Posture. (Developer > Library > Identity Catalog API).
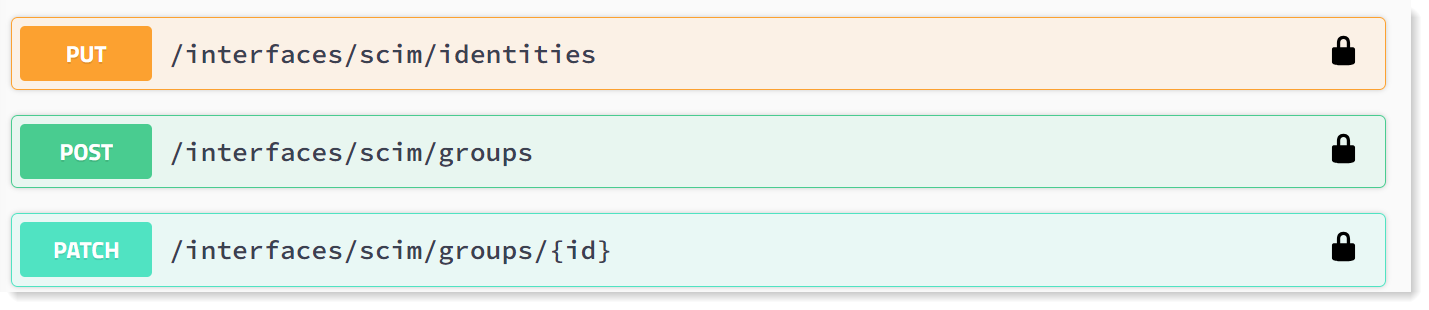
The following are supported:
-
PUT /interfaces/scim/identities: Add and update user information
-
POST/ interfaces/scim/groups: Create a group
-
PATCH /interfaces/scim/groups/(jd): Add or update members in an existing group
You must assign the Identity Catalog Scim Feed Access to your application.
-
In the Proofpoint Developer Portal, select Developer > Authorization > Credentials.
-
Click the Edit Policies
 icon next to the relevant application.
icon next to the relevant application. -
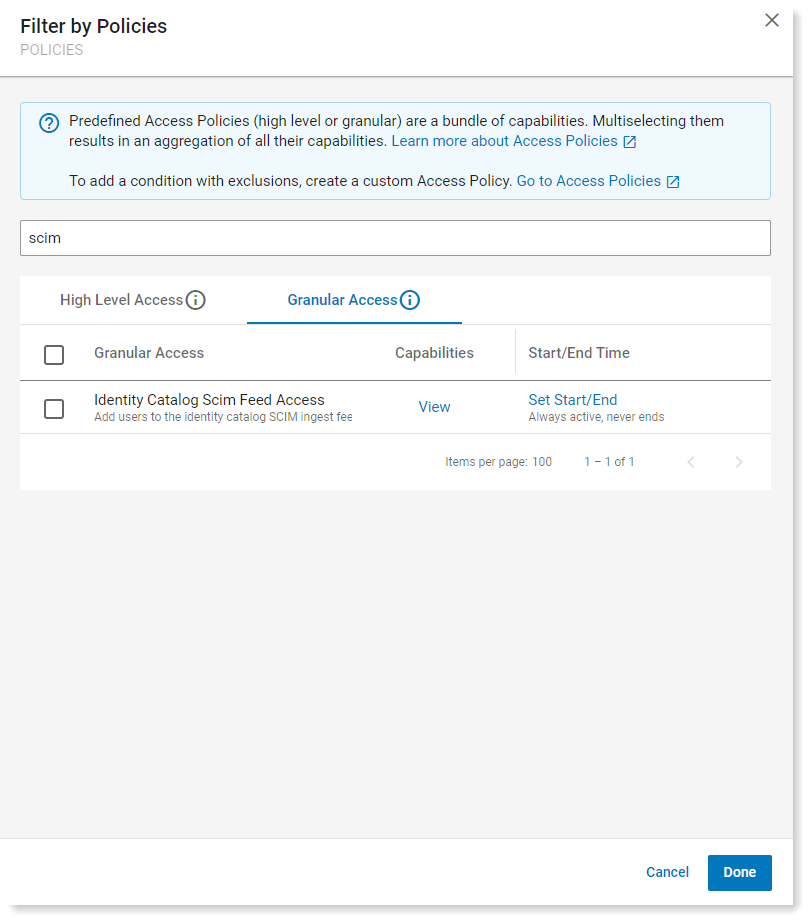
From the Filter by Policies panel, select Identity Catalog Scim Feed Access from Granular Access policies. Click Done.
Examples of Source and Attributes Collected
The table describes some of the user identification attributes collected by each source. In addition other attributes are collected from the sources.
|
Source |
Attribute |
Example |
|---|---|---|
|
Connectors (O365, GSuite etc..) |
|
carol.brown@3z3340.onmicrosoft.com |
|
securityIdentifier |
S-1-12-1-1696632856-1305359795-3721942948-2746764945 |
|
|
Endpoint |
|
carol.brown@3z3340.onmicrosoft.com |
|
Security Identifier |
S-1-12-1-1696632856-1305359795-3721942948-2746764945 |
|
|
SCIM (API) |
email (primary and secondary) |
carol.brown@3z3340.onmicrosoft.com |