ITD User Insights
Proofpoint Identify Threat Defense monitors user behavior patterns across systems. It scans every endpoint—clients and servers, PAM systems and identity repositories to look for unmanaged, misconfigured and exposed identities.
Proofpoint Identify Threat Defense (ITD) Insights provide valuable context about the vulnerability of identities/users. This allows analysts to be proactive in blocking threats before the vulnerabilities can be leveraged for privilege escalation and lateral movement.
Identity Catalog must be enabled.
ITD license is required.
ITD insights are supported providing ITD and Data Security & Posture tenants are hosted in the same region, (for example, US or EU). In case of multi tenancy, for example a single ITD tenant hosted in US, and a single US Data Security & Posture tenant hosted in US is associated with 2 CASB tenants: one in the US region and one in EU - only the US tenants activities will be enriched with ITD insights.
User Insights are stored in the Users Catalog. User Insights are available for creating searches and rules in Proofpoint Data Security Workbench - Explorations and Endpoint Rules (User > User Insights).
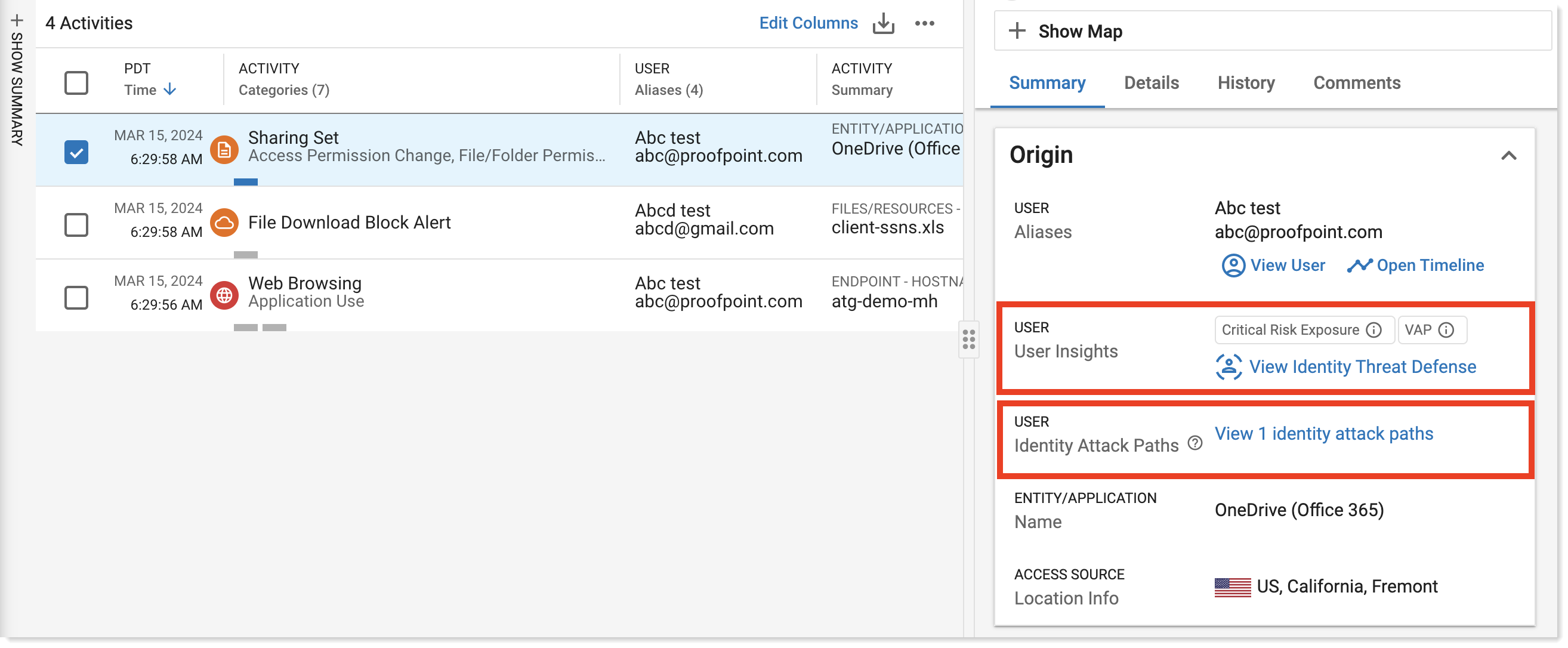
ITD is the source for the User Insights and they are displayed in the Risk Factors and Blast Radius tabs in the User page in the ITD console.
Currently the following ITD User Insights are available:
Other Insights are available from CASB and TAP.
-
Critical Risk Exposure: An identity with Critical Risk Exposure has privileges that can be exploited in the event of an identity breach
-
Privileged Identity: A Privileged Identity has administrative or strong privileges that can be exploited in the event of an identity breach
-
Shadow Admin: A Shadow Admin has unintended or hidden administrative privileges that can be exploited in the event of an identity breach
-
Identity Attack Path: Attack Paths is the number of potential pathways available for an attacker to move laterally using the identity’s stored credentials in the event of an identity breach.
Related Topics: