Agent Integration with Users (Identity) Catalog
When the Agent is integrated with Users Catalog (Identity Catalog), the Agent receives the consolidated user information and uses it with detection and prevention rules.
Users Category may be referred to as Identity Catalog.
User Catalog Information in Prevention Rules
To use User Catalog in prevention rules:
-
Enable User Catalog Integration in the Agent Realm: When processing prevention rules on the Agent, you must enable User Catalog Integration. This setting must be enabled to use the Users Catalog. (Administration app > Endpoints > Agent Realms > Advanced Settings > Processing > User Catalog Integration).
-
Create a prevention rule using User/Group from Catalog.
-
Optionally, you can enrich user information by enabling Enrich User Information from Identity Catalog. (Administration app > Endpoints > Agent Realms > New Realm > General tab.) This setting lets the Agent communicate with the Users Catalog. When enabled, all events are enriched with user information from the User Catalog.
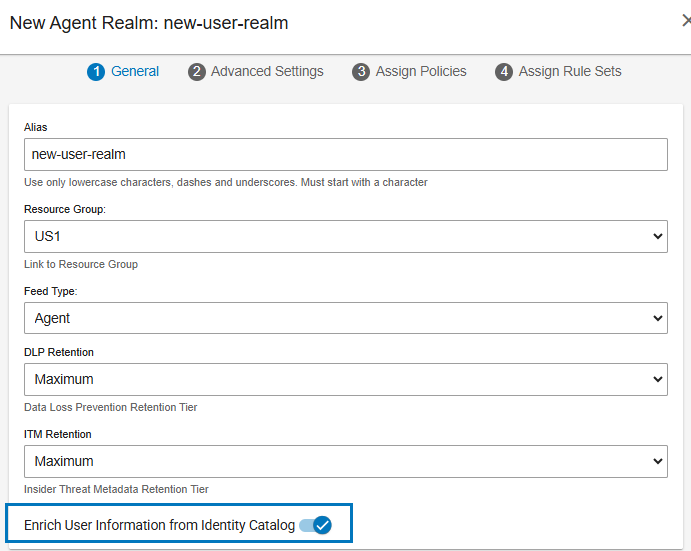
Users and Groups in Users Catalog
User from Catalog and Group from Catalog are available. These fields let you create rules based on the User ID rather than the User Name.
The following describes the User and Group fields and their users:
-
User from Catalog and Group from Catalog: These fields refer to the IDs only and the originate from the Users Catalog.
Use these fields when you want to create rules that target explicit IDs. Since the rule is based solely on the ID, rules remain valid even if you change the User/Group Name.
Rules with these fields are limited to In and Not In operators.
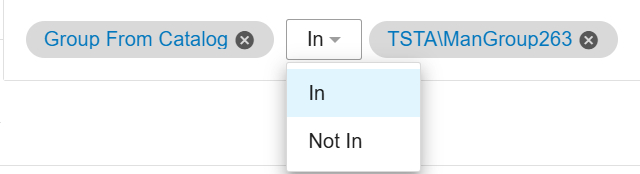
When you create a rule, using these fields, the name is displayed for clarity only.
-
User Name and Group Name: These fields refer to names of the users/groups and originate from Users Catalog or Users Activities.
These fields allow targeting based on pattern matching using wildcard operators (e.g., 'contains').
For example, block all groups where Group Name starts with "admin".
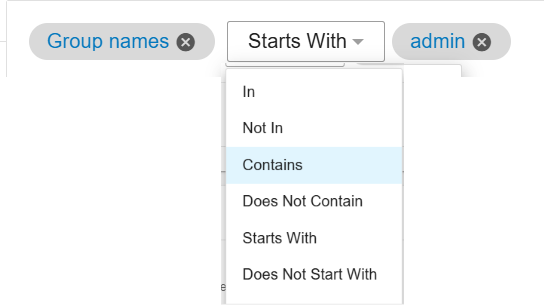
Since these fields are based on the name, if you change the name, the rule will not match.
Mac Agent Integration
When a user logs into a Mac endpoint, the Agent extracts the user information and registers the user with the Identity Catalog. The Identity Catalog then sends the extended user information back to the Agent.
Mac Agents supports the following modes of operations, each with specific user information extraction:
-
Local User (for Mac endpoints not domain-joined): The Agent extracts the local ‘User Name’ from the OS.
-
Domain Joined: The Agent extracts the ‘User Name’ and the ‘Domain Name’ from the OS.
-
Kerberos Single Sign-on (SSO) Extension: The Agent extracts the ‘User Name’ and the ‘Domain Name’ from the Kerberos Certificate. Proofpoint's solution was validated against Kerberos SSO extension, to connect the Mac machine to Microsoft AD, for Azure AD (Microsoft Entra ID) integration.