Metadata Redacted View Restriction Access Policies (Anonymization)
Metadata Redacted View Restriction lets you anonymize user data to protect and restrict sensitive and private data. When applied, the endpoint name/ username is anonymized. Instead of displaying the actual endpoint/username, a unique token is applied to each user, as shown in the example.
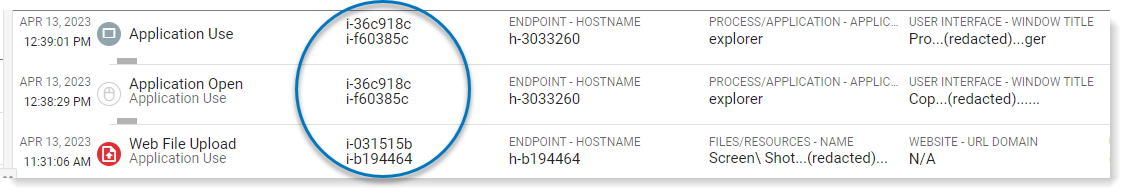
The actual user's identity is hidden so the user's privacy is maintained but the token identifier allows you to continue investigations you need. You can filter by the token identifier as you would an endpoint name or user attribute for filters in Explorations, Rules, and Alerts.
In addition to maintaining the user's privacy, this feature makes sure investigations are objective, since the investigator does not have access to the actual user names.
To use this feature, assign the Metadata Attribute View Redaction Global Restriction policy to the user that you want to restrict. This user will see the anonymized endpoint//user attributes (the token identifier) instead of the actual data.
In Explorations, anonymized fields cannot be filtered as clear text fields.
When assigned to a user, the Metadata Attribute View Redaction Global Restriction policy takes priority over any other assigned policies. For example, a user may be assigned Activity Exploration policy, and then assigned the Metadata Attribute View Redaction Global Restriction policy, the user sees anonymized data.
In Explorations, anonymized fields cannot be filtered as clear text fields.
Creating a Metadata Attribute View Redaction Access Policy
You can create a Metadata Attribute View Redaction - Global Restriction with the parameters you want to anonymize.
-
From the Administration application, select User Management > Access Policies.
-
From the Access Policies page, select New Custom Access Policy.
-
In the General tab, complete the Alias, Name and Description (optional) fields.
-
In the Template tab, click Select next to Template Type.
-
From the list of templates, select Metadata Attribute View Redaction - Global Restriction.
-
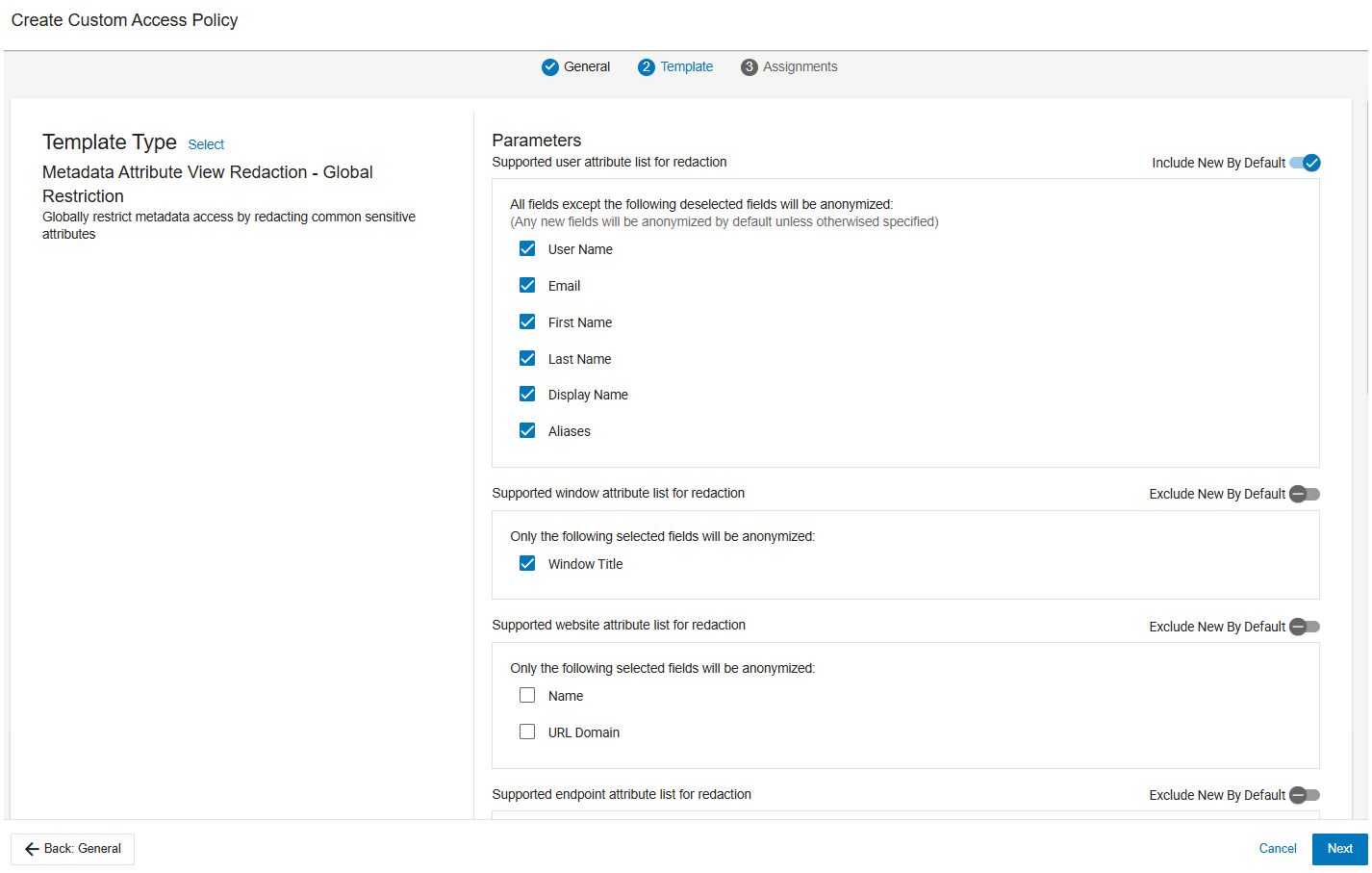
From the list of parameters, select those parameters you want to anonymize.
-
In the Assignment tab, assign this policy to the relevant users, groups and personas.
-
Click Save.
Assigning Metadata Attribute View Redaction Access Policy to a User
You can assign a policy to a user from the list of Users.
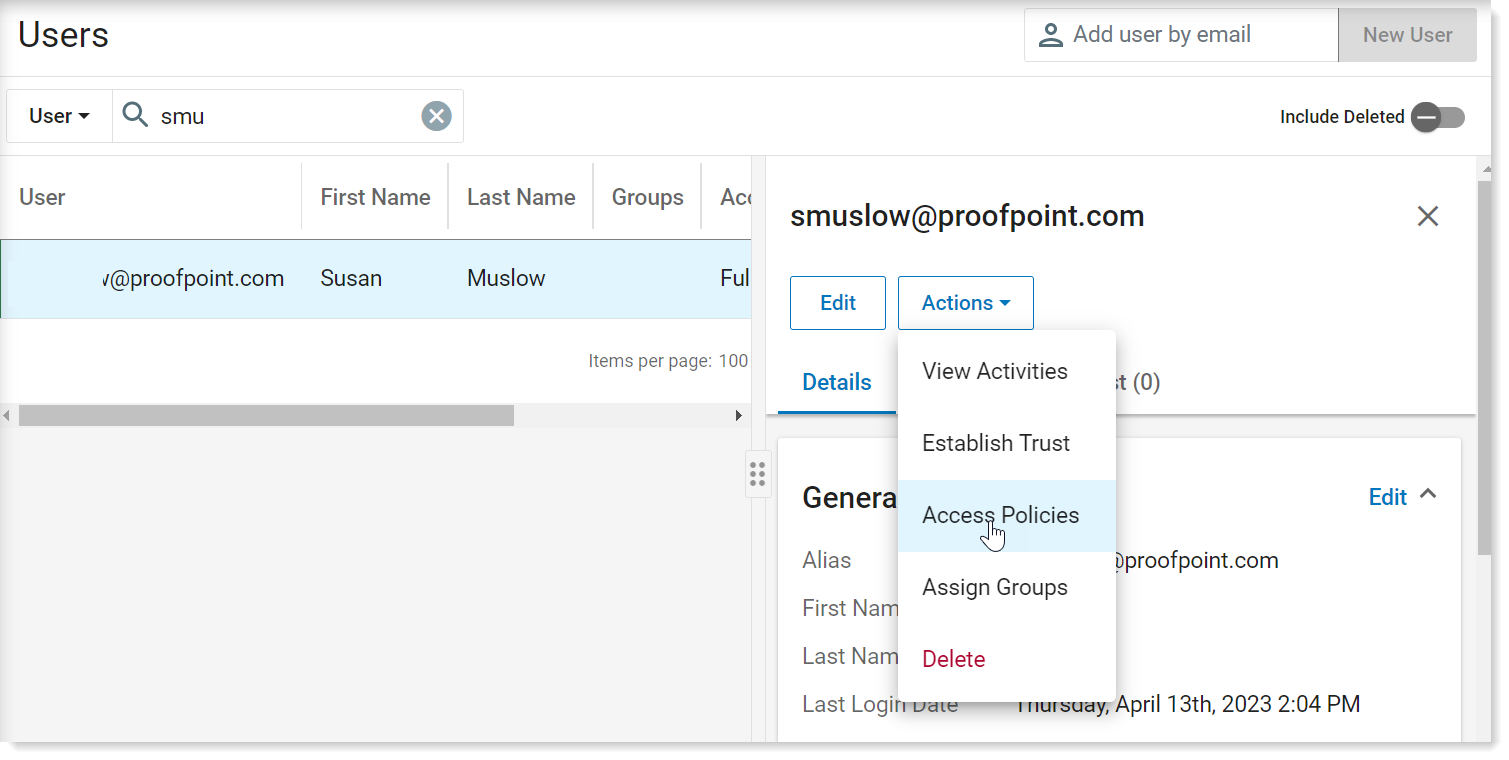
From the Administration application, select User Management > Users. From the list of Users, select the user you want to restrict
In the details panel, from Actions drop down, select Access Policies.
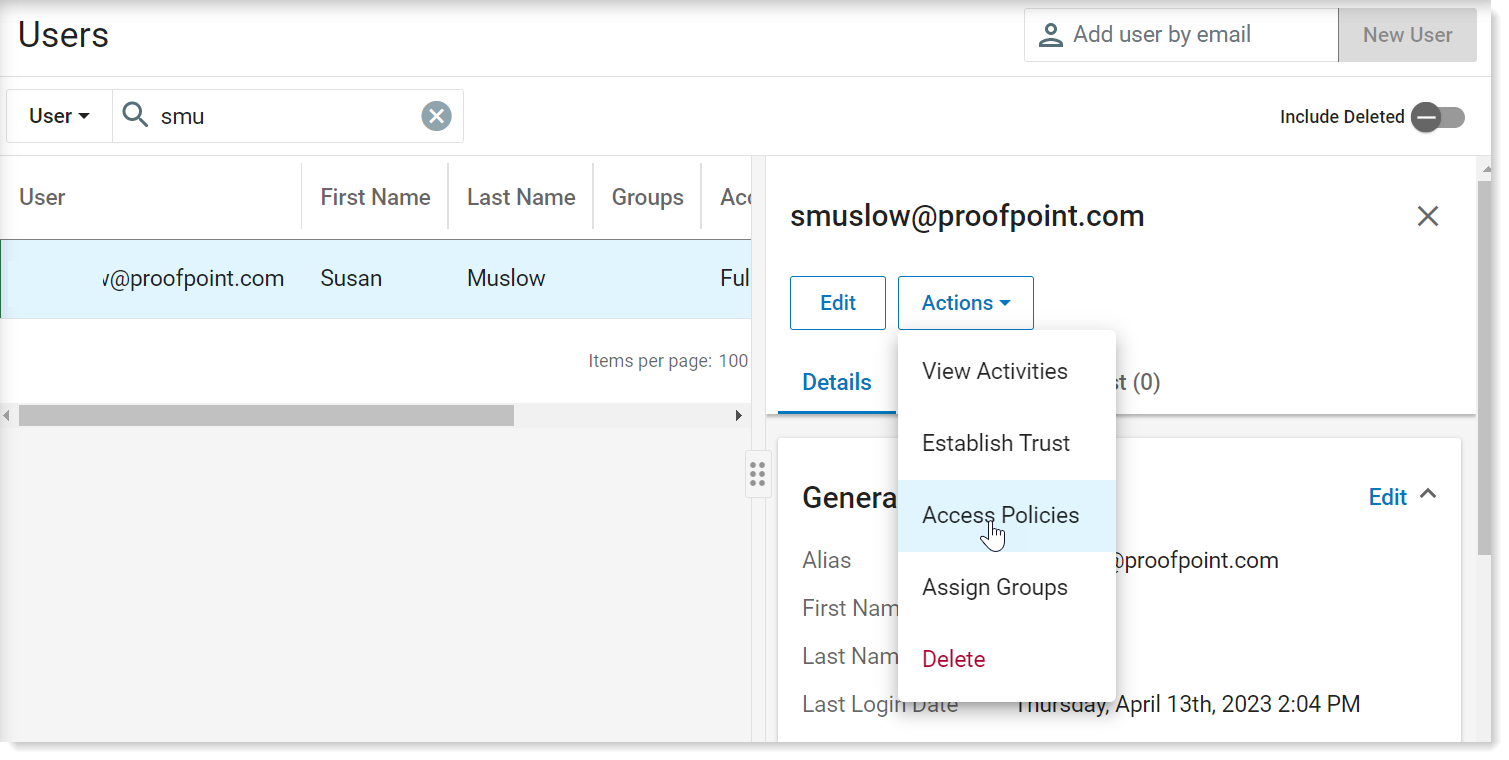
From Granular Access, select Metadata Attribute View Redaction Global Restriction.
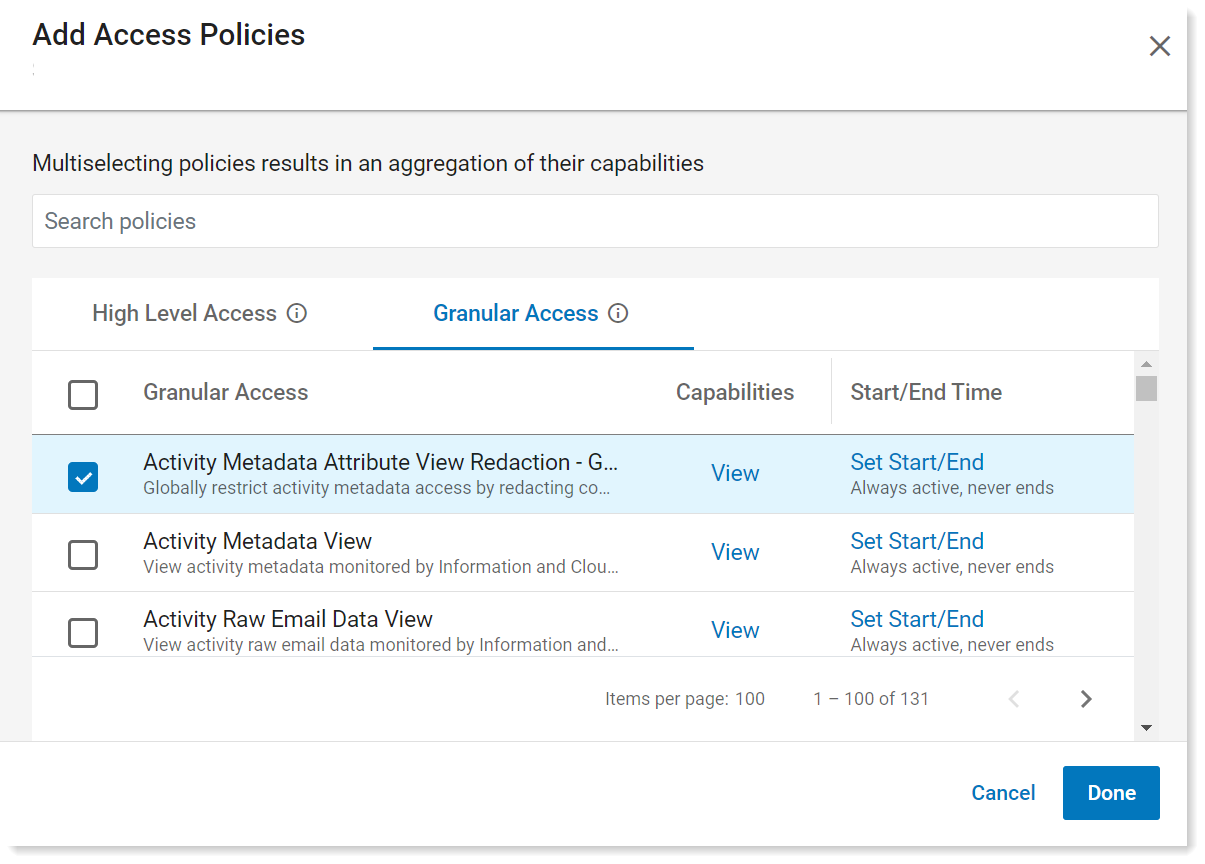
Metadata Attribute View Redaction Global Restriction policy is now assigned to the selected user,
To remove anonymization, simply unassign the Metadata Attribute View Redaction Global Restriction policy.
Parameters for Redaction
You can redact any or all of the following parameters.
User Attributes
User Name
Email
First Name
Last Name
Display Name
Aliases
Identifiers Combinations Field_value
User
Effective User
it.agent.activity.event.executable.owner.user.name._.name.short
Owner Name
Sender ID
Sender Email
Sender Display Name
Window Attributes
Window Title
Endpoint Attributes
Alias
Hostname
FQDN
Name
Activity Service Resource Attributes
Name
Source Name
_derivatives Direction Target Name
Activity Service Resource Path Attributes
Path
Resource URL
Source Path
Target Path
Tracking Origin Resource URL
Permissions Access Identities Alias
Permissions Access Identities Name
Container/Site
Links Access Href
Resource URL Domain
Path
URL
URL Domain
Activity Service Recipient User Attributes
Recipient ID
Recipient Email
Recipient Display Name
Anonymized User Attributes
User attributes are listed in the Capability description of the Metadata ParameterAttribute View Redaction Global Restriction policy.
Select User Management > Access Policies.
From the list of Access Policies click Metadata Attribute View Redaction - Global Restriction.
Scroll down in the General window and click View Capabilities.
Filtering by the Token Identifier
Although a user sees anonymized endpoint//user attributes (the token identifier) instead of the actual data, it is possible to investigate user activity by filtering by token identifiers.
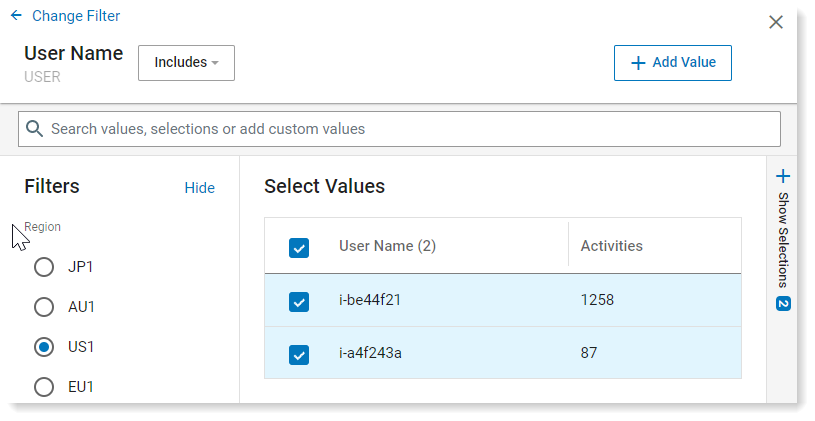
In the example, you want to investigate activity of 2 users.
In an Exploration, select Filter by User > User Name.
From Select Values, select the token identifiers you want to monitor.
Related Topics:
Predefined Access Policies Descriptions