Threat Library
The Threat Library is a collection of common out-of-the box threat scenarios based on research with CERT institute at Carnegie Mellon, NITTF and NIST standards.
You use the rules to create and build new rules. To understand how to create rules from Threat Library items and edit them, see Using the Threat Library.
Threat Library includes prevention and detection rules.
Threat Library rules are associated with a category to help you navigate and see what is available and facilitate using and maintaining the rules .
If you are a DLP only user, the Threat Library currently provides a limited list of data exfiltration rules. (See DLP items.)
The Insider Threat Library is accessed from the Administration app.
All available rules are listed and described in the Threat Library dashboard.
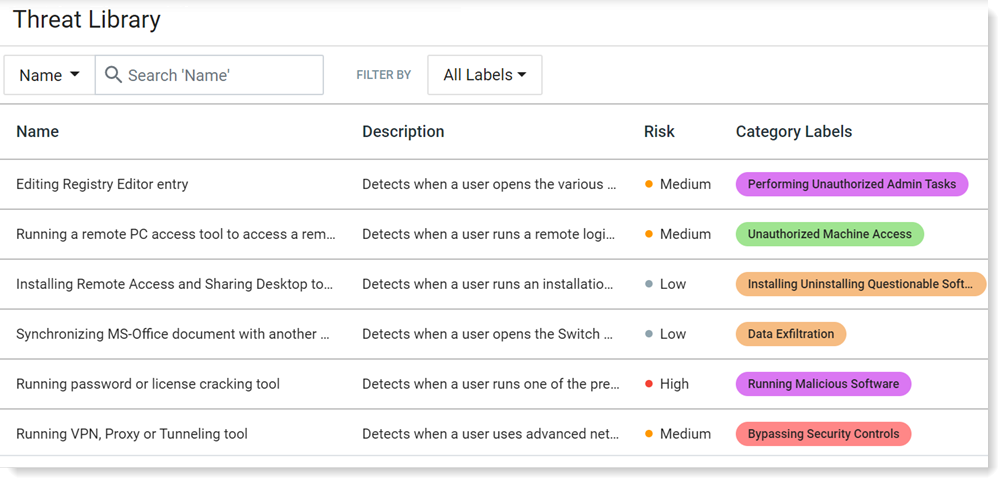
The dashboard includes:
- Description of the threat.
- Risk level associated with the threat (critical, high, medium, low). This is the default recommended value and you can change it when you create a rule.
- Category tags that can be used to help you navigate and use the library.
- Publish date, an indication of what has been added/updated. This lets you see the most recent items added to the Insider Threat Library.
To locate a rule, you can sort the list by name or filter by category label.
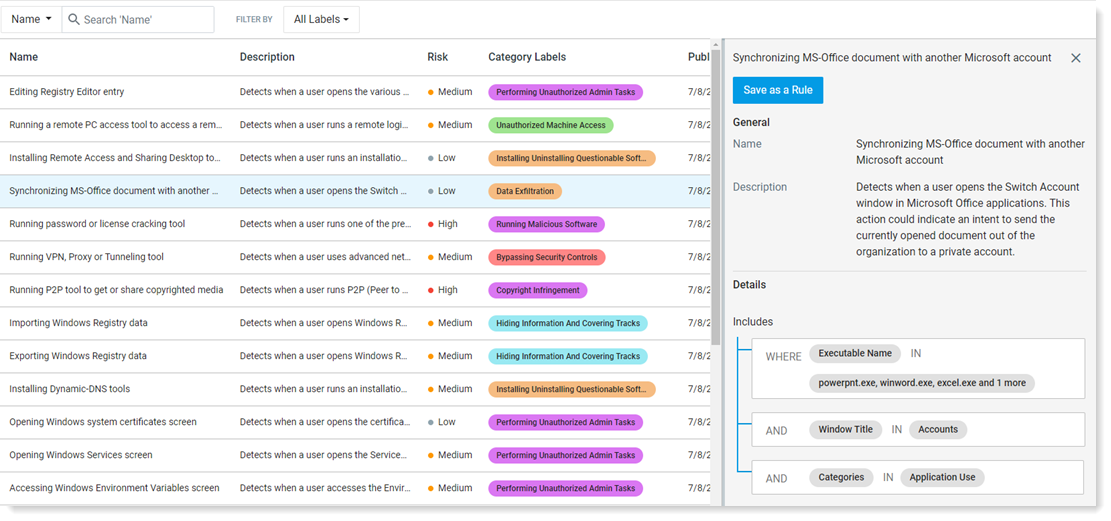
To see more details, click on a rule in the list.
Empty Conditions
You can use empty conditions to create lists that you can use with specific Threat Library detection rules.
For example, to create a rule the detects exfiltration to unauthorized USB devices, you would fill the empty condition with the list of all unauthorized devices.
The following empty conditions are supported:
-
Sensitive Classification Labels
-
Sensitive Content Detectors
-
Sensitive file names or keywords in file names
-
Authorized USB devices
-
Authorized printers
In addition, you can use Encrypted USB devices (by USB Product Name) which is populated with 3 supported USB products.