Inline Authentication and Control rules are applied “inline” with a login transaction, as opposed to the Detection and Remediation rules that are evaluated after a user login has succeeded or failed. Since these rules are applied inline, they can provide real time access control based on context and risk and can prevent suspicious login transactions from succeeding.
Inline authentication and control rule support requires enabling CASB's Adaptive Access Control (AAC) module, which leverages SAML to invoke access. For information about enabling AAC, see the Proofpoint CASB Adaptive Access Control (AAC) and SaaS Isolation Deployment Guide, which is available on the customer community.
Important notes:
-
Rules with remediations and notifications should only be applied following thorough testing in your environment. We recommend that every Detection and Remediation rule should be implemented without remediations or notifications for a period of time, enabling verification that occurrences are as expected.
-
Blocking access control actions should only be applied following thorough testing in your environment. We recommend that you test each rule for a period of time with Allow as the access control and Notifications configured, to verify the occurrences are as expected for the planned policy.
-
The order of the rules in the policy impacts which events trigger which remediations or access controls. Proofpoint CASB evaluates rules from top to bottom.
-
Evaluation stops once a rule with a remediation is matched. For important details about this behavior, see the Managing Inline Rule Policies.
-
For AAC policies, we recommend that you set up a default Allow rule as the last rule in the policy. The default rule should include all users, devices, and contexts, and should be set to Allow
Proofpoint provides best practices for configuring a universally useful policy.
To open the Rule Editor
-
In the main menu, navigate to Policy > Rules.
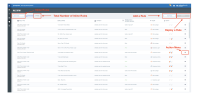
The Rule Editor displays the following information for each rule:
-
Rule Type: The classification of the type of event that triggers the rule. Each rule type is relevant to one or more event types. A list of attributes that refine the type of event that should trigger the rule appear under the rule type. See Defining Inline Rules.
-
Rule Name: A descriptive name for the rule.
-
Context: The conditions on properties of the event that must be true to trigger the rule (for example, specific relevant users, location, or network).
-
Remediation: Automatic defensive responses to the rule being triggered.
-
Alert: The type of alert to be generated when the rule is triggered, and the severity of the alert.
-
Notify: An indication as to whether email notifications are sent on alert generation. Notifications can be sent to administrators
 or to the user
or to the user  who triggered the rule.
who triggered the rule.