Agent Install Mac SSO and Active Directory
This topic describes how to set up Kerberos SSO Extension from your organization's local Active Directory. Kerberos Single Sign-on (SSO) Extension allows users to authenticate seamlessly to domain resources, if the machine is not domain joined.
Proofpoint's solution was validated against Kerberos SSO extension, to connect the Mac machine to Microsoft AD, for Azure AD (Microsoft Entra ID) integration
The Kerberos SSO Extension links to Active Directory. It requests/renews Kerberos tickets and syncs the user’s AD password back to their local user account on the Mac. The Kerberos SSO extension was created to enhance Active Directory integration from a local account.
The following is the suggested practice is to create a local account on Mac with same username as the AD username.
JAMF Portal Setup
This describes the Kerberos SSO Extension configuration in JAMF. You need to modify the domain details and push the profile using an MDM (such as JAMF).
-
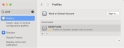
From the JAMF Web console dashboard, click the Computer > Content Management and select > Configuration Profiles from the menu on the left-side. The Configuration Profiles screen displays.
-
Click New to add a new Profile.
-
In General Settings section:
-
Name: Set a name for the profile, for example “Kerberos SSO Extension”
-
Level: Select Computer Level
-
Distribution Method: Install Automatically
-
-
In Single Sign-On Extensions section click Add and update the following fields:
-
Payload Type: Kerberos
-
Realm: Type your domain name with Upper Case characters only.
-
Hosts: Type your domain name with Lower Case characters, and dot at the beginning, for example: .mydomain.net
-
Mark as default realm when more than one Kerberos extension configuration exists: Ignore
-
Automatically use LDAP and DNS to determine the Kerberos extension's AD site name: Enforced
-
Automatic login: Allow
-
User presence to access the keychain entry: Skipped
-
Local password sync: Enable
-
-
In Scope section:
Assign the target computers that this profile will apply to, depending on your organization structure you can choose to apply to all computers that enrolled to Jamf or to specific computers.
Enrolling to JAMF from the Endpoint
This describes how to enroll to JAMF and synchronize the passwords.
-
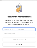
Open a browser and browse to: https://your-jamf-url/enroll
-
Authenticate and enroll.
-
Install the downloaded profile file.
-
After installation is completed, confirm that your computer appears in JAMF computers inventory.
-
If you want, you can apply the Configuration Profiles to a specific computer by adding the machine to the scope:
Configuration Profiles > Kerberos SSO Extension > Edit > Scope > Add
-
After 1-2 minutes the Sign-in pop-up will appear.
-
A screen will appear, showing Sign into Your Domain Name, in the Username field, enter the AD credentials when prompted.
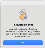
After you enter your AD credentials, the Kerberos SSO Extension will synchronize your macOS login password with your Kerberos (AD) password.
A Password Synchronization message displays.
-
To confirm that the synchronization works, the you can test by logging out and back in to the macOS device.
You will get the following message:
-
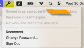
In the upper bar, you will see the following:
-
To confirm that Kerberos ticket has cached to the local machine, open Terminal and type the command klist.
You can see the domain user’s Kerberos ticket that cached locally.
Related Topics:
Mac Agent ITM/ Endpoint DLP Bundle Installation