Overview
One of the potential security risks an organization can face comes from the authorized third-party applications connected to their cloud environment. This is especially true when third-party apps are granted permission to perform activities that can put an organization, its data, and users at risk.
Proofpoint researchers observed that abused 3rd party application attacks (malicious and legitimate) impacted 10% of organizations (2024). Learn more about these unique attacks, vectors, and campaigns discovered by Proofpoint cloud research in the Proofpoint blog.
The Proofpoint CASB and TAP Account Takeover solutions support 3rd party app governance & threat detection.
Use the 3rd Party Apps page to identify and govern third-party applications (3PA) and reduce the potential attack surface while supporting business needs using safe applications:
-
See when new third-party applications are added to your environment.
-
Identify all high-risk 3rd third party applications authorized in your environment.
Use the Data Security Workbench app to identify and respond when:
-
An external threat actor performs an account takeover, then either authorizes a malicious third party app or abuses a legitimate third party app to gain persistent access to resources. (Persistent access means the access granted to the app remains regardless of password reset and/or MFA setting changes to the authorizing user.)
-
A real user mistakenly authorizes a malicious app
For more information, see the Understanding 3rd Party App Activities section of this help topic.
Terminology
What is a 3rd Party Application?
3rd party applications (also known as 3PA, OAuth, or Connected cloud applications) are applications that your users or admins authorize for productivity. These apps may have access to valuable resources in your M365 or Google Workspace environment, such as files and email.
What are Scopes?
Scopes are the different types of permissions a third-party application may be granted. Based on the nature of the app and types of activities it may ask permission to perform, some types of scopes are considered high-risk.
For example, the following scopes are considered to be high risk:
-
Send mail on behalf of others
-
View all content in tenant Google Workspace scopes
-
Manage delegated admin roles for your domain
-
Audit emails of users on your domain
-
Manage the provisioning of users on your domain
-
Manage your Identity and Access Management (IAM) Policies
3PA Permission Types in Microsoft 365 (Overview); How to view permission types (Steps)
Because third-party apps request numerous permissions (aka scopes), they present a tangible risk to organizations operating SaaS applications.
Using the 3rd Party Apps Page
Use the 3rd Party Apps page to make an informed decision whether to assign a “Blocked” or “Approved” classification to all third-party applications in use by your organization.
Blocking an application is implemented as follows:
-
In Microsoft:
-
This action permanently blocks all users from using the application (even if they are assigned to it.)
-
To view Microsoft’s ‘Enabled for users to sign-in’ setting, navigate to Microsoft Entra ID > Enterprise Applications > Application Properties.
-
-
In Google Workspace:
-
This action includes revoking all existing permission grants, and revoking any new authorization grants by the Proofpoint policy rule ‘Block All Blocked Apps’.
-
Enabling the policy template ‘Block All Blocked Apps’ as the first rule in the Application Governance rules section is mandatory for correct implementation of 3rd party apps classification.
Block All Blocked Apps rule must be configured at the top of the list
You can document classification considerations in a comment and signify when an application is under review.
This page also allows your security analysts to:
-
Be notified of Classification Drifts:
-
This includes situations when an application that was previously approved now requires higher permissions than those originally granted, or now includes additional risks, such as a potentially malicious domain associated with it.
-
-
View any open tasks that require maintaining including:
-
Newly authorized applications
-
Application's whose classification did not technically succeed (Failed status)
-
Application whose approval has drifted (Changed status).
-
-
Interact with the application page by:
-
Filtering, adding columns and sorting to customize a view which is useful for your classification purposes.
-
Highlights display all apps that meet the selected filter criteria above the highlight area AND any filters applicable in the insight. Clicking on a highlight display element adds filters to the filter area (in some cases this results in OR condition, grid results may be different than insight display). For example, when filtering on the Productivity Category, the Gen AI insight displays Productivity apps with Gen AI or Gen AI enhanced categories.
-
Clicking the See all link, adds Gen AI and Gen AI enhanced to the Category filter which results in displaying apps that are Productivity OR Gen AI OR Gen AI enhanced.
-
-
Receive insight indications about the app, its users, and scopes to quickly understand the nature of an application and its associated users.
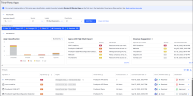
Third-Party Apps Page
The Third-Party Apps page is accessed from Data Security Workbench > SaaS Security > 3rd Party Apps.
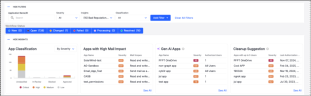
Insight Panel
The Insights Panel includes interactive filters with links that let you quickly drill down into specific risks. This helps prioritize cleanup to reduce your attack surface with less effort.
The Insight Panel provides visibility into:
App Classification Status: Shows how many apps are unclassified, in review, blocked, or approved. Organizations should aim to review all apps - and at minimum, prioritize those with high severity - and classify them as either Approved or Blocked to strengthen governance and reduce risk.
Apps with High Mail Impact: Spotlights apps with risky email access scopes like “send mail as user”.
Gen AI Apps: Identifies apps using or enhanced with generative AI capabilities (M365 only).
Cleanup Suggestions: Detects high-severity apps with few users and old authorization dates that may be safe to remove.
Third-Party Apps Catalog Table
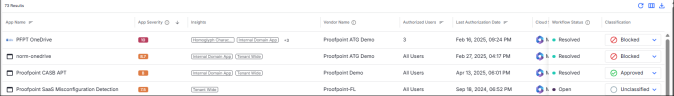
For each third-party application connected to your cloud environment, the Third-Party Apps Catalog table displays the following information:
-
App Severity: This score represents the highest severity observed in your organization. It considers various data points, including:
-
Permissions granted to the app.
-
App prevalence in the community.
-
Is the publisher verified by Microsoft (in Microsoft environments).
-
Threat insights found in the app's parameters, such as scopes or reply URLs. (Visible also in the Forensics section)
-
-
App Type: The platform on which the application is based, such as desktop, mobile.
-
Application: The name and logo of the third-party application.
-
Authorized Users: The number of users in your organization that use the application.
-
Category: The classification of the application, such as games, business and finance.
-
Cloud Service: The SaaS application with which the application is associated.
-
Comment: User comments regarding the application.
-
Community Last Authorization: The most recent time authorization activity for a third-party app among Proofpoint’s customer base.
-
Community Prevalence: Prevalence levels reflect how widespread the application is compared to other applications among Proofpoint’s customer base.
-
First Discovered: Date the system discovered the app in your organization’s environment.
-
ID: The unique global identification number assigned to the app by the cloud service.
-
Insights: Important attributes detected about the app. For example: Malicious, Malicious Domain, Tenant Wide, Scope Resemblance, Homoglyph Characters.
-
Last Authorization: The most recent time authorization activity for a third-party app.
-
Scope Category: General category of the type of permissions used by the app., such as SharePoint, Teams, Mail, Contacts, Groups and Users, Openid, Permission Granting, Time Management.
-
Vendor: Vendor name based on information provided by the vendor to the cloud service.
When you first display the table, it shows default columns only and is sorted by severity and last authorization date.
-
Click the ||| button to add, delete, or change the order of columns.
-
Use the available filters to quickly view apps according to your specified criteria or by the current workflow status assigned to the app.
-
Click Export to download a .csv file of the apps and columns currently displayed in the UI.
Understanding Workflow Status
You can view where the system is currently for each app by viewing its assigned workflow status:
-
Resolved: successfully classified
-
Open: not yet classified
-
New: not yet classified, app first discovered in the last 14 days
-
Changed: app severity level has increased since classification and requires review
-
Processing: classification is in progress Vs the Cloud Service
-
Failed: classification has failed to be updated in the Cloud Service
Understanding 3PA Severity Scoring
Proofpoint’s sophisticated third-party application risk scoring model factors in the following:
-
Permissions Required by the App
-
Includes fine grained permission support
-
Each permission (aka scope) is rated according to potential impact and rarity
-
All permission types are supported, including user/admin delegated permissions and application-only permissions (M365)
-
Permissions on all resources are supported. In M365, this includes both Graph and Azure resources.
-
The score considers permissions actually granted in your environment only (and not a global score based on what the application potentially requires by default).
-
-
Commonality of the App
-
How common is the app across the landscape? For example, an application that is popular among thousands of tenants is scored lower than a rare application.
-
-
Signs of Being a Potentially Malicious App
-
Proofpoint’s real-time detection also uses innovative threat indicators, which can suggest an app may be malicious with varying levels of confidence. Some of these indicators leverage unique and proprietary Proofpoint threat intelligence. For example:
-
Is the publisher/vendor verified by Microsoft?
-
If an application includes a URL that Proofpoint’s Targeted Attack Protection (TAP) deemed malicious
-
If an application is registered to a new domain according to Proofpoint Digital Risk
Additional licenses are not required to benefit from intelligence leveraged from other Proofpoint services.
-
-
Different authorization events for an application made by different users may include different required permission scopes and insights. This page displays information about permission scopes, insights, and forensics, which represents the highest severity observed during recent authorization events, as well as all currently authorized permission scopes.
Viewing Third-Pary App Information
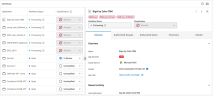
Click on an individual app in the table to view its detailed information in the side panel.
Detailed information is provided in the following five tabs:
-
General: Provides a detailed overview of the 3PA, recent activities, and community analysis, (for example, aggregated data regarding the app from the Proofpoint customer base). Use the edit feature in this section to add a comment.
-
Authorized Scopes: Shows detailed information for all permissions in use by the app, including:
-
Total number of scopes
-
Total number of scopes in each severity type
-
All related scopes categories
-
All individual scopes
-
Total number of “Application Only” scopes. (Application-only permissions allow a 3rd party app to act on resources directly, using its own identity, and not as a delegated user/account. Application-only permissions can only granted to a third-party app by an administrator, and are typically granted to core enterprise applications.)
-
-
Authorized Users: Lists users of the third-party application and their details. Applications may be authorized for all users in your organizations (tenant-wide insight). Individual user authorizations may exist in addition to All users authorizations. Filter by user name, email or group to locate an authorized user.
-
Forensics: Provides a description of all threat insights automatically detected for the app, and why the insights suggest the application may be malicious.
-
Vendor: Displays vendor name and details are based on information provided by the vendor to the cloud service. Vendors that are verified by Microsoft are displayed with a verification icon. Learn more about Microsoft vendor verification.
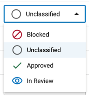
Assigning App Classifications
Use the drop-down menu in the Classification column to switch a current classification to a different classification option. The following classifications are available: Blocked, Approved, Unclassified, In Review.
Changing a classification option may yield a change to the apps workflow status.
Understanding 3rd Party App Activities
3rd Party App Access Authorize activities include information about the application that was authorized in this activity. Scope categories and severity values displayed are relevant specifically to this activity and the permissions and application parameters that are part of this activity, whereas the 3rd party application page, that can be reached by clicking on the application name, displays the overall state of this application in your environment. For example the severity field includes the highest severity considering all user and admin authorizations.
Clicking on the application name in activities opens the Third-Party Apps page filtered by the application. Select the application row to view additional details about the application.
The Trigger field includes information on the activity source:
-
Originated by audit inspection - the activity information was provided by the cloud application via API as party of activity audit trail.
-
Originated by comparison analysis - Activity audit trails provided via the audit API are sometimes late or fail to arrive. In order to ensure 3rd party application data is fully aligned with the cloud application, a daily process inspects the current authorizations that exist in the cloud application and analyzes for potential gaps. Gaps result in an activity with the Originated by comparison analysis trigger type. The activity time is the process run time and not the actual time the user authorized the application, in this case.