This topic describes some of the differences in terminology between the CASB application and Proofpoint Data Security & Posture dedicated Data Security Workbench app.
Since Proofpoint Data Security & Posture hosts not only cloud activity, but also, ITM, endpoint DLP, and email DLP, with more Data Security & Posture channels to come, it requires a terminology that applies equally to all these channels
CASB Alert Tagging in Data Security Workbench
When viewing CASB alerts in Data Security Workbench, you will see each comes with predefined tags.
The mapping between the CASB rule types and Analytics predefined tags is as follows:
-
Access Rule -> Suspicious Login tag
-
Data Rule -> Data Leakage tag
-
App Governance -> Suspicious Activity tag
-
Configuration & Security Posture Rule -> Suspicious Activity tag
Common/Frequently Used Cloud Event Attribute Names in Data Security Workbench
This table lists key cloud event and alert attributes in the Data Security and Posture platform for CASB and ATO Protection customers.
Some of the attributes in the below table are not available for all cloud activities.
|
Section Name |
Attribute Name |
Example Values |
Description |
|---|---|---|---|
|
Activity |
Primary Category |
Successful Login, File Modify, File Upload, File Share. |
Defines the specific type of user activity such as login, file upload, or sharing. |
|
Activity |
Action Family |
Change, View, Directory |
Groups similar types of actions, such as changes, views, or deletions. |
|
Activity |
Action Object Type |
Storage File/folder, Directory Login, Third-Party-Application, Mail mailbox |
Specifies the type of object impacted by the activity (e.g., file, login, 3rd-party app). |
|
Activity |
Action Status |
success, failure |
Represents whether the action completed successfully or failed, as reported by the cloud provider. |
|
Activity |
Action Status Message |
Error validating credentials due to invalid username or password |
Detailed message from the cloud provider explaining the reason for action failure or providing additional information about the action. |
|
Activity |
Target Application/ Resource Name |
{{3rd Party App Name}} |
Name of the third-party application targeted by the action. |
|
Activity |
Target Application/ Resource Severity |
Low |
Risk level or severity of the third-party application involved. |
|
Activity |
Resource Insights Key |
share with |
Additional types of insights representing the activity provided by Proofpoint |
|
Activity |
Resource Insights |
All-Domain-Share, Internal Share, Public Share |
Activity insights value (Share level, 3rd party app name, etc.) |
|
Activity |
Resource Type |
Direct Access Sharing Link |
Additional information about the type of object that has been created/modified. |
|
Activity |
Resource Attributes |
permission:reader Scope Category |
Additional attributes about the resource created/modified. For file share activities it is used to describe the type of sharing permission created/modified. |
|
Activity |
Resource Attributes |
Resource Attributes Transition |
User friendly view of changed attribute values |
|
Activity |
Resource Relation Labels |
acme.com |
The domain of collaborators involved in file sharing activities. |
|
Activity |
Resource Relation Object Alias |
jdoe@acme.com |
The email addresses of collaborators in file sharing activities |
|
Activity |
Session id |
1.92847E+12 |
Unique session identifier for tracing login or access events. |
|
Client / 3PA |
Client / 3PA Alias |
51c4d537-d0d8-4523-bd82-54f70c75d3b0 |
Identifier of the client application that performed the action |
|
Client / 3PA |
Client / 3PA Name |
lucidchart |
Name of the client application that performed the action |
|
Client / 3PA |
Risk Level |
Low |
Risk level of the client application that performed the action |
|
Client / 3PA |
ID |
third_party_app_b2c097db5acb54d706ae7ac562c1bbd6 |
Proofpoint app identifier of the client application that performed the action |
|
Client / 3PA |
Client / 3PA Type |
mobile |
Type of interface used to access the app (e.g., mobile, script). |
|
User |
User properties |
Internal, External Resolved, Unresolved |
Specifies whether the user is internal or external.Unresolved: user does not match a known domain user External: guest or external user. |
|
User |
Directory Department Name |
Finance |
User's department, as defined in the organization’s directory (EntraID) |
|
User |
Directory Title |
Sales Person |
User’s title as defined in EntraID |
|
User |
Directory City Title |
San Fransicso |
User’s city as defined in EntraID |
|
User |
Directory Country Code |
OM |
User’s country code as defined in EntraID |
|
User |
Overall Risk Level |
Low |
Overall risk score calculated for the user by Proofpoint Human Risk Explorer based on behavioral and contextual analysis |
|
User |
Threat / Awareness / Data Risk Level |
Low |
Risk score under a specific risk dimension (e.g., data, threat., awareness) as defined in Human Risk Explorer |
|
User |
Directory Manager Catalog ID |
e6eae7e3-2a1d-4dc4-8a48-238eb25623da |
Unique identifier of the user's manager as defined in EntraID |
|
Entity/Application |
Suite |
Salesforce, Office 365, Google Workspace |
Cloud provider name |
|
Entity/Application |
Name |
OneDrive (Office 365), Microsoft Teams (Office 365) |
Specific cloud application name (for some cloud apps its similar to the suite field (cloud provider name) |
|
Access Source |
Client IP |
106.201.198.123 |
IP address of the actor/user from which the user activity originated |
|
Access Source |
User Agent |
Microsoft SkyDriveSync 25.110.0608.0001 ship; Windows NT 10.0 (22631) |
User agent reported by the actor |
|
Access Source |
Client Device |
Desktop, Mobile |
Device type the actor based on its user agent |
|
Access Source |
Client OS |
Windows Mac |
OS of the actor’s device based on its User Agent |
|
Access Source |
Host IP domain |
Aitrel.in |
Domain of the ISP based on the actor’s IP address |
|
Access Source |
Host IP ISP Name |
Bharthi Airtel ltd. |
Name of the ISP based on the actor’s IP address |
|
Access Source |
Country/City/State |
India, Mumbai |
Country/city/state of the actor user based on its IP address |
|
Access Source |
Location Info |
India, Maharashtra, Mumbai |
Aggregated location field (country, region, city) based on actor’s IP address |
|
Session |
ID |
08108dc9-eaa9-07de-b416-82b54ce2fc7a |
Session identifier (if exists). Several events can be performed as part of the single session |
|
Resource |
Name |
testfile.docx |
File name |
|
Resource |
Resource URL |
https://acme-my.sharepoint.com/personal/sitename/Documents/user/file.docx |
File’s full URL |
|
Resource |
Resource URL domain |
https://acme-my.sharepoint.com |
Domain part of the file based on its URL |
|
Resource |
Path |
Documents/username/folder/file.docx |
File path |
|
Resource |
Container/Site |
acme-my.shrepoint.com/ |
Name of file container such as sharepoint site Onedrive or Shared drive |
|
Resource |
Parent Folder |
folder/file.docx |
File’s folder name |
|
Resource |
Classification Labels Name |
Credit Card number, Classified, |
Name of matching Detectors, Data Class and Classifiers, MIP labels or Google badged labels |
|
Resource |
Classification Labels Type |
AI Classifier, Detector, MIP |
Type of data classifier matching the file’s content |
|
Resource |
Classification Labels confidence score |
77 |
AI classifier score |
|
Resource |
Share Level |
Internal, Exernal |
Calculated share level of file or content |
|
Resource |
Owner Name |
jdoe@acme.com |
File owner email address |
|
|
|
|
|
|
Resource |
Content Type |
image/jpeg, application/pdf |
MIME type of file |
|
Resource |
Extension |
jpg |
File extention |
|
Resource |
Hash Values |
|
File’s Hash value (SHA256 or quickXor) |
|
Resource |
ID |
2363cbcde7648ad96478f3f43d385427 |
Proofpoint file identifier |
|
Resource |
System Origin Identifier |
6aaddb60-3163-4c58-93dc-21266be0587b |
Cloud Provider file identifier |
|
Feed |
Region |
US1 |
Data center region in which the data is persisted in |
|
Feed |
Tenant Alias |
Acme |
Data Security Platform tenant name |
|
Feed |
Tenant ID |
203208323 |
Data Security Platform tenant identifier |
|
Organization |
Instance Name |
ACME corp. |
CASB tenant name |
|
Organization |
Instance ID |
casb:tenant:tenant_ca1812b7c73ae4c48bd8d9fe0cc12b188 |
CASB tenant identifier |
|
Event |
Occurred Time |
Sun, Jul 6, 2025 10:55:45 AM UTC |
Time of actual activity (as captured by the cloud provider). |
|
Event |
Observed Time |
Sun, Jul 6, 2025 10:55:45 AM UTC |
Time of actual activity (as captured by the cloud provider). Same as Occurred Time |
|
Event |
Ingested Time |
Sun, Jul 6, 2025 10:55:45 AM UTC |
Time Proofpoint algorithms identified the activity as a threat during automatic threat detection. In the case of a file related event, this represents the time in which file threat/content scanning was completed and the event became available in Data Security Workbench application |
|
Event |
Inspected Time |
Sun, Jul 6, 2025 10:55:45 AM UTC |
Time the event became available to Proofpoint by the cloud provider via API |
|
Event |
Updated Time |
Sun, Jul 6, 2025 10:55:45 AM UTC |
Reflects the last detection time, in the event of a threat information update |
|
Event |
ID |
flevent_fba5dfb24f99d124e5d0232a2ae9bd36 |
Proofpoint internal event identifier |
|
Alert |
Severity |
Low |
Alert’s severity |
|
Alert |
Rule Name |
RuleName |
Name of the matching rule triggering the alert |
|
Alert |
ID |
alert_d87fcdcae91449dc530241cb31bf4232 |
Alert identifier |
|
Alert |
Description |
|
Triggered rule description |
|
Alert |
Remediation Type |
File:apply Google Labels |
Name of remediation action that was executed |
|
Alert |
Remediation Status |
Success, Failed |
Status of remediation action that was executed |
|
Alert |
Remediation Executed Time |
Tue, Jun 3, 2025 7:05:10 PM GMT+3 |
Time in which the remediation action was triggered |
|
Alert |
Remediation Updated Time |
Tue, Jun 3, 2025 7:05:10 PM GMT+3 |
Time in which the remediation action status was updated |
|
Alert |
Remediations - Message |
{{message}} |
Remediation status message |
|
Alert |
Remediation Origin Type |
remediation:automated, remediation:manual |
Indicates if the remediation action was triggered manually or by a rule (automatic) |
|
Indicator |
Type |
CASB rule, Detector, Dictionary, SmartID |
Vector representing all match critertias that were matched by the rule |
|
Indicator |
Indicator/Detector Name |
{{RuleName}}, {{MIPLabelName}}, {{Detector Name}}, |
For alerts: alert name For MIP labels: Label name |
|
Indicator |
Matches Object Type |
event:match, File:content |
vector representing the type of each match criteria |
|
Indicator |
Matches Object Name |
Activity Type, Exclude Networks, Result |
vector representing the names of the rule’s match criteria |
|
Indicator |
Matches Params Value |
Add Mailbox Delegation, Dictionary_CreditCard,SmartID_CreditCardNumber |
vector representing the values of matched attributes |
|
Indicator |
Matches Results |
Add Mailbox Delegation |
|
|
Indicator |
Matches Results Stats Count |
N/A, 9, 8, 15 |
Vector representing the number of matches per Indicator |
|
Additional Information |
Threat Score |
50 |
Proofpoint threat detection risk score |
|
Additional Information |
Login Status |
Faliure |
Login activity status |
|
Additional Information |
Risk Level |
Low |
Proofpoint threat detection risk level |
|
Additional Information |
Owner |
jdoe@acme.com |
File owner email address |
|
Correlations |
Object ID |
flevent_a46d61adf490f3cc0e509125b917ca9b |
Correlated event identifier |
|
Processing |
Processing Action / Response |
Make File Private |
Indicates the result of a remediation action |
|
Processing |
Action Executied Time |
Tue, Jun 3, 2025 6:51:56 PM GMT+3 |
Time in which the response action was initiated |
|
Processing |
Action ID |
remediationaction_2652cf83b8423efa61bd0cf4b423b922 |
remediaiton action identifier |
Key Examples
Cloud Service -> Entity/Application Name
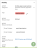
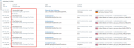
The legacy CASB Activities, Alerts, and Files pages use the term 'Cloud Service' to designate cloud application monitoring by CASB-sanctioned applications.
In the Data Security Workbench Explorations page, this is now called the Entity/Application Name, and is found in the Activity Summary column and the Summary panel, as shown below.
Event Types -> Primary Category and Action Families
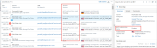
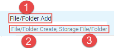
The legacy CASB Activity page featured both a column and filter called 'Event Types'(1) that showed groups or families of events. This example illustrates the Change (2) event type. It displays different types of changes, such as (3) File/Folder Rename, File Modify, or User Update. These specific types of changes all come under the general 'Change' family.
In the Data Security Workbench Exploration page, these specific types are translated into primary categories, which are grouped into families. There are several levels of families, as you will see in the query example below.
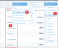
The first column in the grid displays the category information.
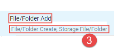
Refer to the example below. The bolded text is the primary category. That is the specific type of event that took place ('File/Folder Add'(1)). Below the primary category, is the lowest level family ('File/Folder Create (2)) and the type of object (Storage 'File/Folder (3)) or resource, as they were called in CASB.
The primary categories are similar to the specific events that appeared in the event type column in the legacy CASB activities: file rename, file update, etc.
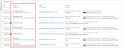
Resource Types -> Objects
The legacy CASB used the term 'resource type' to designate the object on which an event took place, such as a file, a third-party application, or a user. In the Data Security Workbench Explorations page, these are called 'object types' (3).