Adaptive Risk Policies
The Adaptive Risk Policies feature enables dynamic application of rules for Proofpoint CASB and ATO Protection based on users' risk profiles defined in Proofpoint Nexus People Risk Explorer (NPRE). This integration empowers security administrators to leverage user risk assessments, improving threat response and enhancing protection against data loss by risky users.
NPRE is a Proofpoint product that collects data and signals from various Proofpoint products. NPRE provides detailed risk categorization using multi-dimensional models (vulnerability, privilege, and attack risk). For more information about NPRE, see NPRE Guide in the Proofpoint Community.
Adaptive Risk Policies dynamically apply CASB rules based on these risk profiles, addressing challenges in managing static group-based security models.
Adaptive Risk Policy key capabilities include:
-
Adaptive Rule Enforcement: Automatically adapts CASB rules to users' changing risk profiles.
-
Enhanced Risk Awareness: Utilizes NPRE’s risk scores and target groups (e.g., Imminent Targets, Privileged Users).
-
Simplified Administration: Reduces reliance on static AD groups, streamlining policy updates and maintenance.
-
Dynamic Response: Prioritizes alerts and apply dynamic remediation actions based on user risk levels.
NPRE Risk Groups and Adaptive Risk Policies
Risk Groups are configured in Proofpoint Nexus Risk Explorer based on:
-
Risk Profiles: Custom groups of users defined by NPRE admins based on various risk factors, such as:
- Monitoring data (email, domain, directory, or custom group membership)
- Privilege data (business function, seniority, management chain)
- Vulnerable risks (frequent DLP alerts, phishing simulation failures, email clicks).
User risk evaluations occur daily, dynamically assigning users to one or more profiles.
-
Target Groups: Pre-defined risk categories provided by NPRE to classify users based on their risk levels. User memberships are dynamically updated daily using new data from Proofpoint products.
Adaptive Risk Policies Use Case Examples
The following are some examples:
-
Restrictive File Sharing: Block external file sharing for users with a high number of DLP violations or failed security training.
-
Account Takeover (ATO) Prevention: Automatically suspend accounts of users considered are “Imminent Targets” with multiple failed login attempts.
-
Apply Policies on Custom Groups of Users without making changes to Active Driectory: Create dynamic risk profiles in NPRE for departments without dedicated AD groups (e.g., county departments).
-
Tailored User Notifications: Send targeted warnings to users in the "very privileged" risk profile when they authorize high-risk third-party applications.
-
Prioritized Alert Triage: Focus on alerts for users with critical risk profiles, such as "Imminent Targets" or "Data Exfiltrators."
Setting Up Adaptive Risk Policies
Prerequisites:
-
An active license for Nexus People Risk Explorer.
-
Existing Risk Profiles in Nexus People Risk Explorer. For more information on how to create a risk profile in NPRE, see Viewing Risk Profile.
-
Access the Rule Editor
-
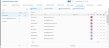
Navigate to Policy > Rule Editor in the Cloud App Security Broker (CASB) application.
-
In the Rules dashboard, click Add Rule.
-
-
Set up the Rule
-
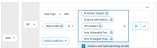
In the Rule Templates dashboard, select the rule type (Access, Data, App Governance or Configuration and Security Posture)
-
Select Add New Rule to create a rule.
Alternatively, you can select a predefined rule template for risky users, e.g. the VAP or Risky User Account Takeover template and modify the selected risk profiles as needed.
-
Complete the Name and Description section.
-
Complete Application and Activity Type section.
-
-
Risk-Based Criteria
When creating a new risk profile in NPRE, it takes up to 24 hours for the risk profile to be available for selection in CASB rules
-
Rule Logic
-
Continue defining the rule logic by combining risk-based attributes with existing conditions using logical operators (AND/OR).
-
For example, you can restrict external file sharing for users with a profile of Very Vulnerable People" having multiple DLP violations.
-
-
Response and Remediation
-
Save the rule and ensure it is active.
-
Test the rule to confirm expected behavior.
Best Practices
-
Regularly review NPRE risk profiles to align with evolving threats.
-
Combine adaptive rules with CASB's content-based policies for comprehensive security.
-
Monitor the Identity Catalog to ensure risk group data is up-to-date.
Related Topics: