Detecting Credit Card Exfiltration
In this example, credit card data exfiltration is detected. Exfiltration may be through upload or USB copy.
For this example, Content Scanning must be enabled.
It is recommended that setting up this case, after the Agent has been collecting information for a few days. Then generate a few sample events to confirm the use case configuration works correctly.
In this example, content scanning has been enabled in the Agent Realm with the following options:
-
Scan Triggers: All scan triggers are selected
-
DLP Detectors: Credit card number is a selected value
-
Snippets: Enabled
Get Started
Set up the Exploration to detect Web File Upload activity.
-
Open a new Exploration. From Proofpoint Data Security & Posture, select the Data Security Workbench app.
-
From the left-side-menu, select Activity > Explorations. Click New Exploration button.
-
Your new exploration opens and you see the source node with the default region, time and source. By default, a new Exploration shows all events captured for the past 24 hours, without any filtering applied.
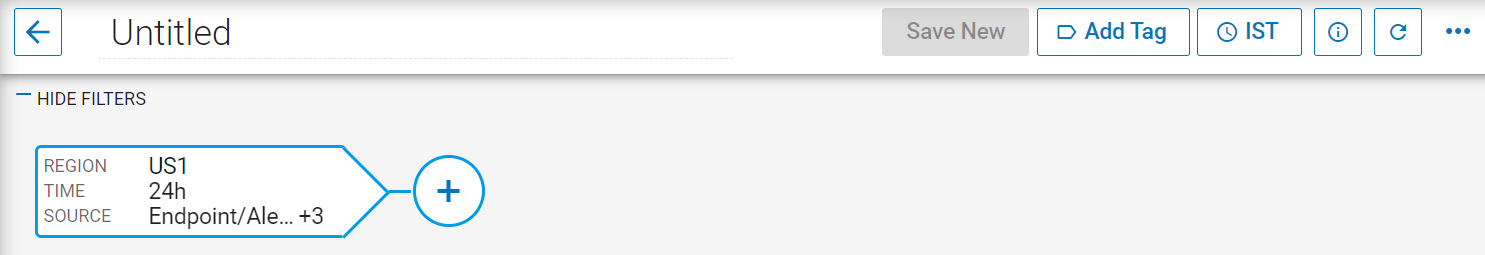
-
Hover over this first filter and click the pencil button to edit the filter.
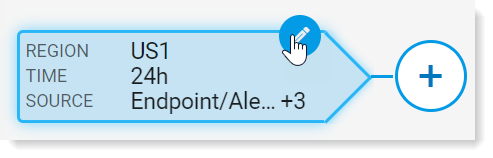
A pane on the right opens.
-
In the Filter by > Time area, in Over the last, select 7d. All the data over the past 7 days will display. Click Done.
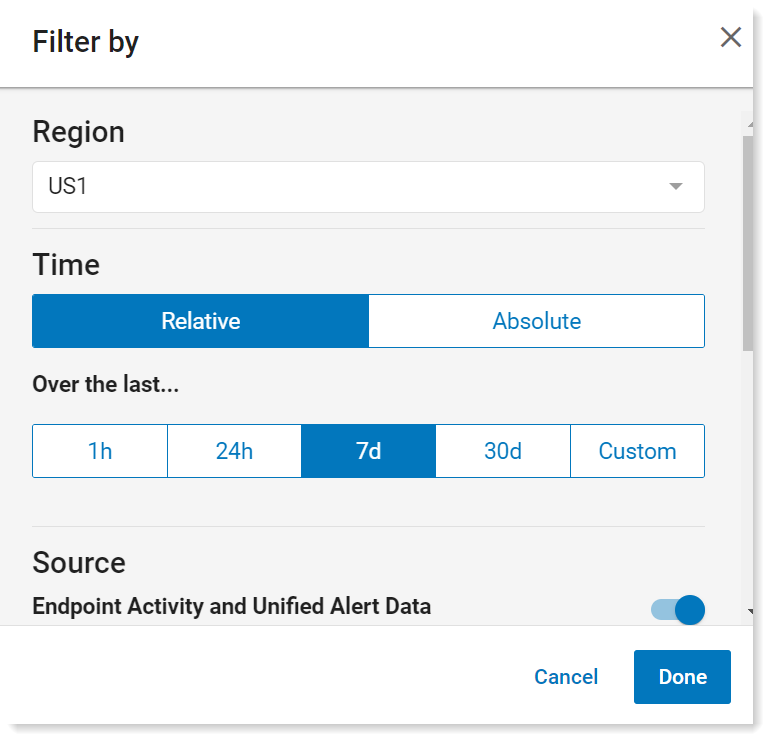
-
Now, define the activities. Click + (add filter button) to add a new filter. A pane opens on the right.
-
Select Primary Category > Web File Upload and Copy to USB.
Type Primary Category in Search Fields to locate this field.
If Detector is not available, you do not have an Content Scanning events in our current timeline. Either expand the first filter’s time range filter to include more days or generate a sample event of file upload or USB copy with credit card data in it.
-
Click + (add filter button) to add a new filter. This is the detector you want to use. Select Indicator > Type > Detector,
-
From the list, select the values you want. For this example, select credit card number and then click Done.
-
You see the results in the table.
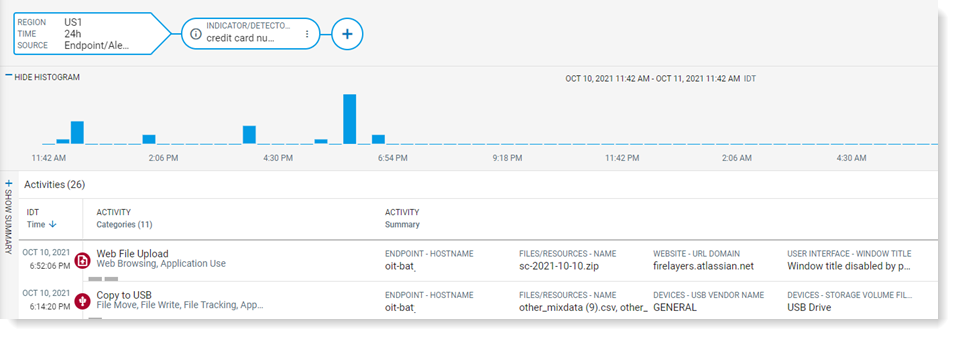
-
Click any result to see more information.