Proofpoint Isolation Analytics
All Isolation end-user and system events are shown in the Data Security Workbench app. Use the out of the box Explorations for Isolation to quickly find the events that are important to your organization.
For example:
-
Isolated URLs: TAP URL Isolation – this will show all corporate email clicks that were Isolated.
-
Isolated Pages: Phishing Blocked – this will show all pages visited in Isolation that were blocked because the system detected phishing lures.
-
Isolated File: Blocked by File DLP Scan – this will show all file uploads/downloads that were blocked in Isolation because scans detected sensitive content in the file.
Isolation Exploration Templates
Pre-configured Exploration Templates
Pre-configured Exploration Templates Dozens of pre-configured Exploration templates are available to help you quickly carve out the top events customers are interested in viewing, including:
| Exploration Template Name | Description | License Type |
|---|---|---|
| Isolated File: Allowed by File DLP Scan |
Files that contained sensitive data and were allowed. |
|
| Isolated File: Allowed by File Threat Scan | Files that contained malware and were allowed. |
|
| Isolated File: Blocked By File DLP Scan | Files that contained sensitive data and were blocked. |
|
| Isolated File: Blocked by File Threat Scan | Files that contained malware and were blocked |
|
| Isolated Pages: Phishing Blocked | Files and URLs blocked due to phishing. |
|
| Isolated Pages: Spam Blocked | Files and URLs blocked due to spam. |
|
| Isolated URLs: All Activities | Files and URLs that were isolated. (All Isolation Channels). |
|
| Isolated URLs: All Threats Allowed | Files and URLs that contained threats and were allowed. |
|
| Isolated URLs: All Threats Blocked | Files and URLs that contained threats and were blocked. |
|
| Isolated URLs: All Threats Detected | Files and URLs that contained threats. |
|
| Isolated URLs: Blocked By Policy | Files and URLs blocked by Isolation policies. |
|
| Isolated URLs: Blocked By Reputation Check | Files and URLs blocked due to an existing threat. |
|
| Isolated URLs: Blocked By Threat Scan | Files and URLs blocked due to threat scan finding phishing, malware, spam, or other threats. |
|
| Isolated URLs: Compromised Senders | URLs sent to corporate email from a compromised sender and opened in Isolation. |
|
| Isolated URLs: Excluded From Isolation | URLs that opened in the user's native browser due to an exclusion policy. |
|
| Isolated URLs: Malware Blocked | Files and URLs blocked due to malware. |
|
| Isolated URLs: SaaS Isolation | All activity in SaaS Isolation. |
|
| Isolated URLs: TAP Clicks Protected | Initial URLs redirected from corporate email to TAP URL Isolation. |
|
| Isolated URLs: TAP URL Isolation | All activity in URL Isolation, including the initial redirected URLs from corporate email to TAP URL Isolation. |
|
| Isolated URLs: Uncategorized | URLs that have yet to be categorized. |
|
| Isolated URLs: User Exited to Native Browser | Files and URLs redirected to Isolation then opened in native browser. |
|
Custom Explorations
To quickly find specific events not covered by an existing exploration template, build a customer exploration by:
-
Starting a new exploration from scratch, or
-
Launching an exploration template that mostly closely matches what you are trying to find, then modify its filters.
After building a custom exploration, save it as new exploration so you can easily refer to it in the future.
Common/Frequently Used Isolation Exploration Filters
This topic describes some of the differences in terminology between Isolation and Proofpoint Data Security & Posture dedicated Analytics app. Common/Frequently Used Cloud Event Attribute Names in Analytics
| Data Security Workbench App Filter Used in Isolation Explorations | Used to Filter the Following: | Example of Values | JSON Path |
|---|---|---|---|
| Region | Region The Info Protection data center region which holds user events (*required in first filter node) | US1, EU1, AU1, JP1 | feed.region |
| Time | The timeframe when events occurred (*required in first filter node) | 1 hour, 24 hours, 7 days, 30 days, Custom | event.occurredAt |
| Source | The source of the events (*required in first filter node) | Isolation | entityType |
| Product | All licensed Isolation services that capture user events. Use this to filter for "Isolation" if you specify multiple sources. | Isolation | feed.product |
| Feed -> Type | The Isolation channel (determined by the user activity) | proofpointisolation.com, urlisolation.com, saasisolation.com | feed.kind |
| Activity -> Primary Category | The type of user activity in the Isolation browser | Web Browsing, File Upload, File Download | activity.primaryCategory |
| Processing -> Action Reasons Indicator Labels Value | The action taken by the Isolation system based on the policy that was applied | Threat Scan, Reputation Check, Isolation Policy/Role, DLP Scan | processing.actions[].reasons[].indicators[].labelsp[].value |
| Files / Resources -> Classification Labels Name | The classification of threat as determined by the Isolation system's scan | Spam, Malware, Phish | resources[].classification.labels[].name |
| Files / Resources -> Resource Type | The type of URL that had a policy applied |
Page; File; iFrame; Request Note: ‘Request’ filters for initial URL clicks in TAP protected emails |
resources[].kind |
| Processing -> Enforcement Action / Response | The action taken by the Isolation system based on the policy that was applied | Isolation-Allow, Isolation-Block, Isolation-Exit | processing.actions.kind |
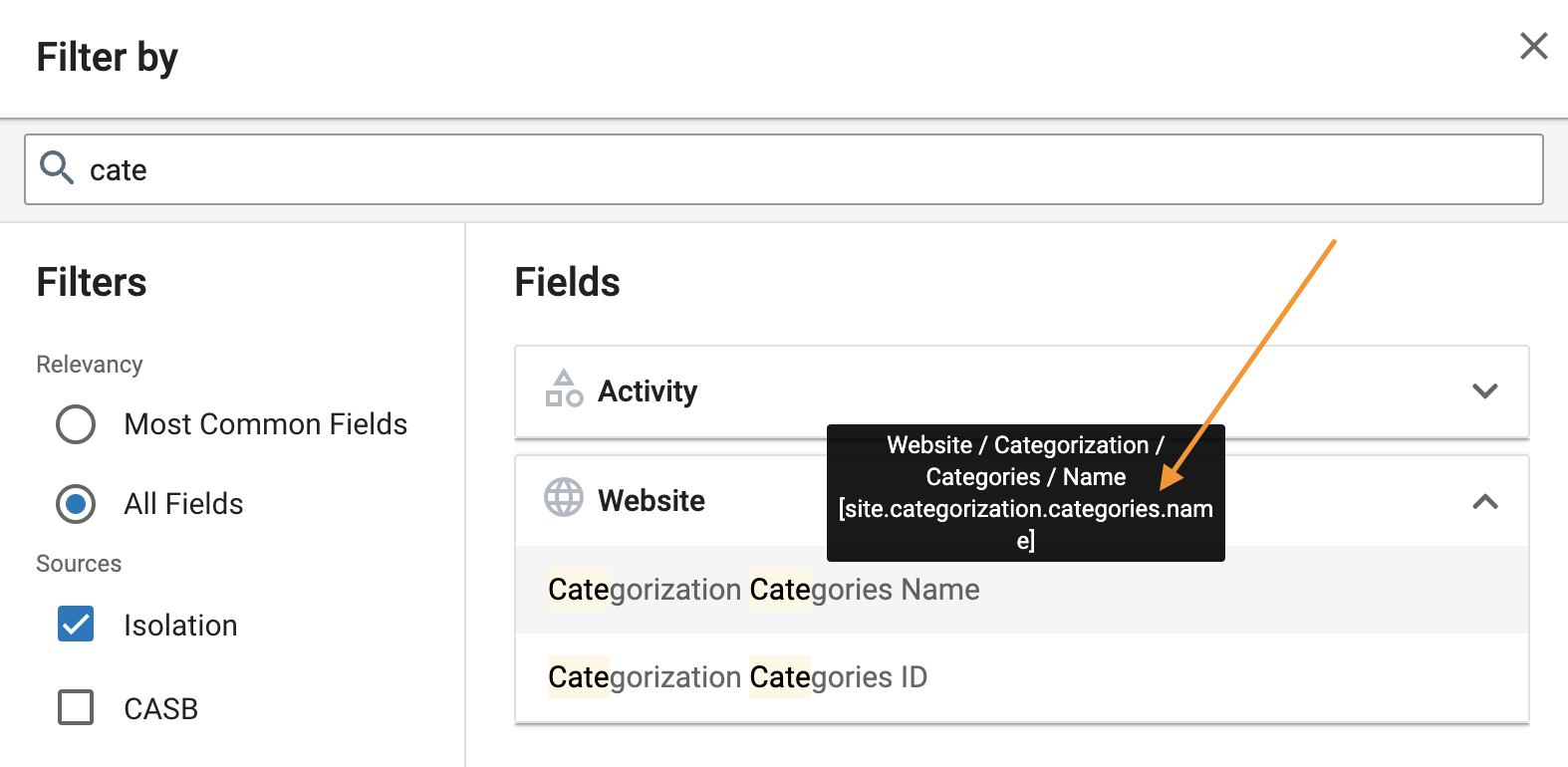
| Website -> Categorization Categories | The assigned web content categories to isolated URLs | Uncategorized, Malware sites, Phishing and Other Fraud | site.categorization.categories[].name |
| Indicator -> ID | Include or exclude a specific filter parameter in the exploration | pfpt:isolation:rule:include, pfpt:isolation:rule:exclude | indicators[].id |
You can view the JSON Path by hovering your mouse directly over the field.
Isolation Exploration Example
Isolated Pages: Phishing Blocked
In this Proofpoint Isolation exploration example, we will walk you through the steps required to create an Exploration that shows all pages and files visited in Isolation that were blocked because the system detected phishing lures.
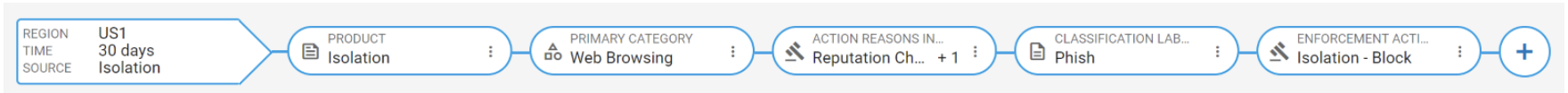
The complete filter will look as follows:
Steps
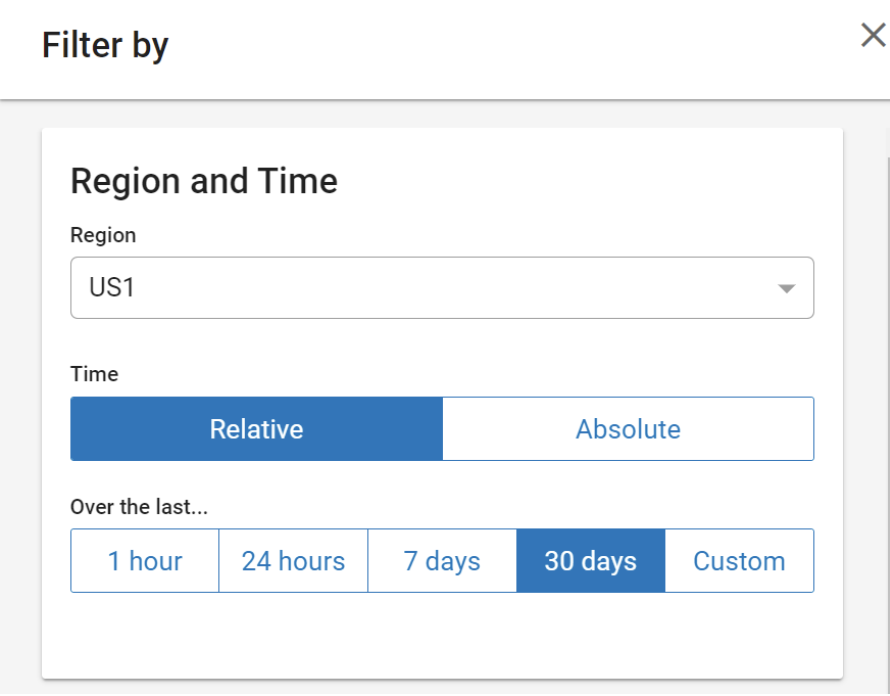
1. Edit the initial source node to match with Region: US1, Time: 30 days, Source: Isolation.
2. Add a new filter, then search for field ‘Product’ in the ‘Feed’ card. Select ‘Isolation’.
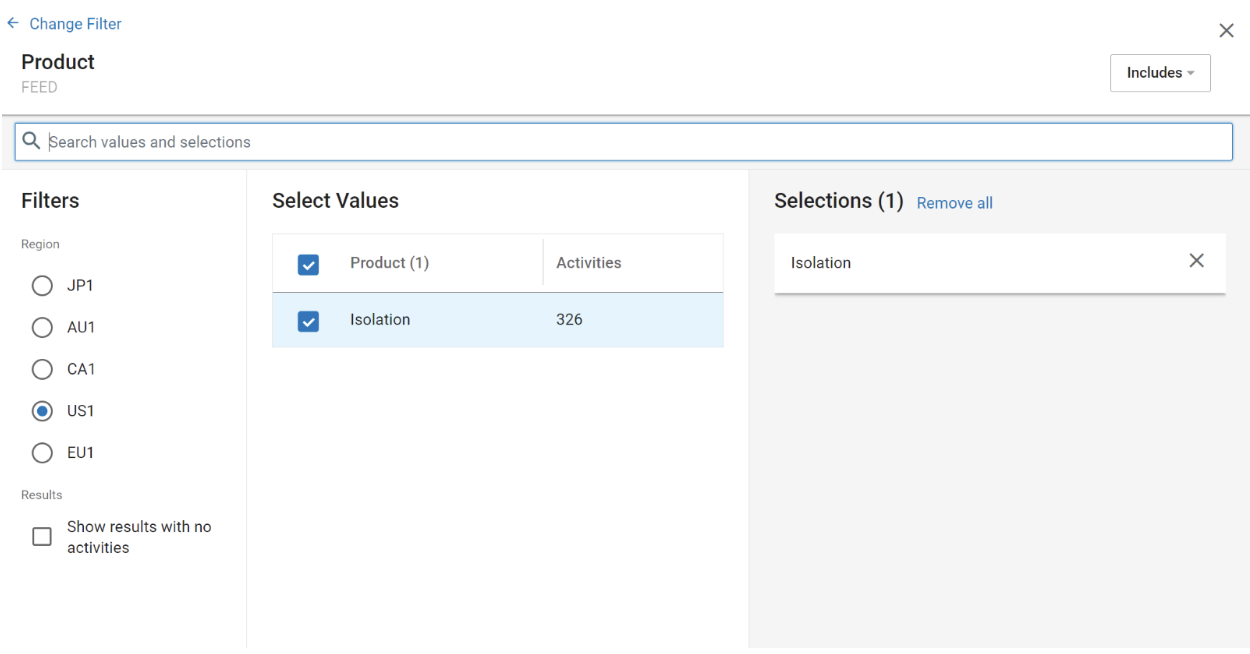
If the Source Node specifies Isolation as the source, you do not need to also specify Isolation as the product. If the Source Node does not specify Isolation as the source, step 2 is required.
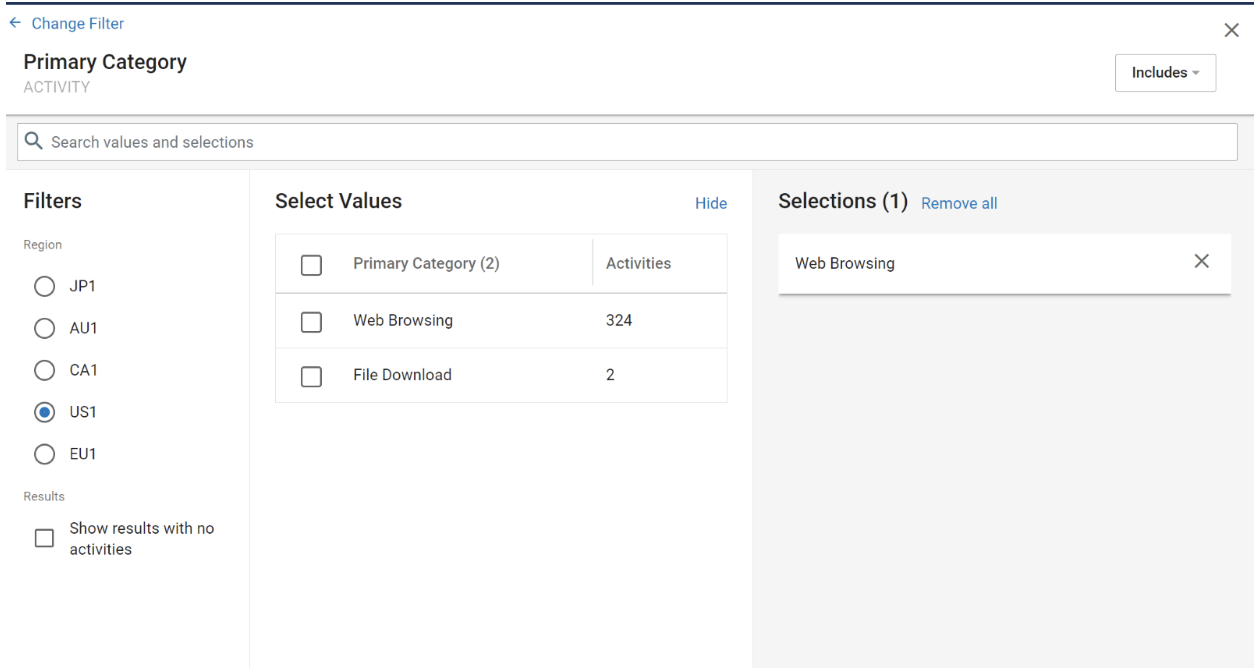
3. Add a new filter, then search for field ‘Activity’ in the ‘Primary Category’ card. Select ‘Web Browsing’
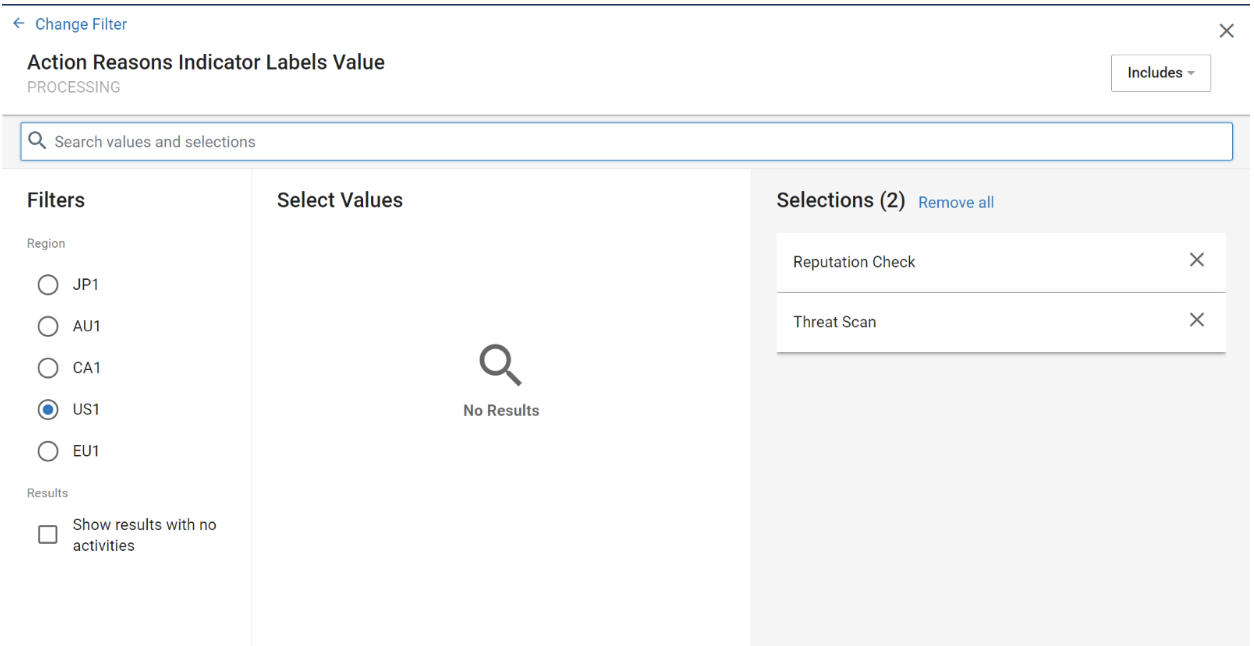
Add a new filter, then search for ‘Action Reasons Indicator Label Value’ from the ‘Processing’ card. Select ‘Reputation Check’ and ‘Threat Scan’.
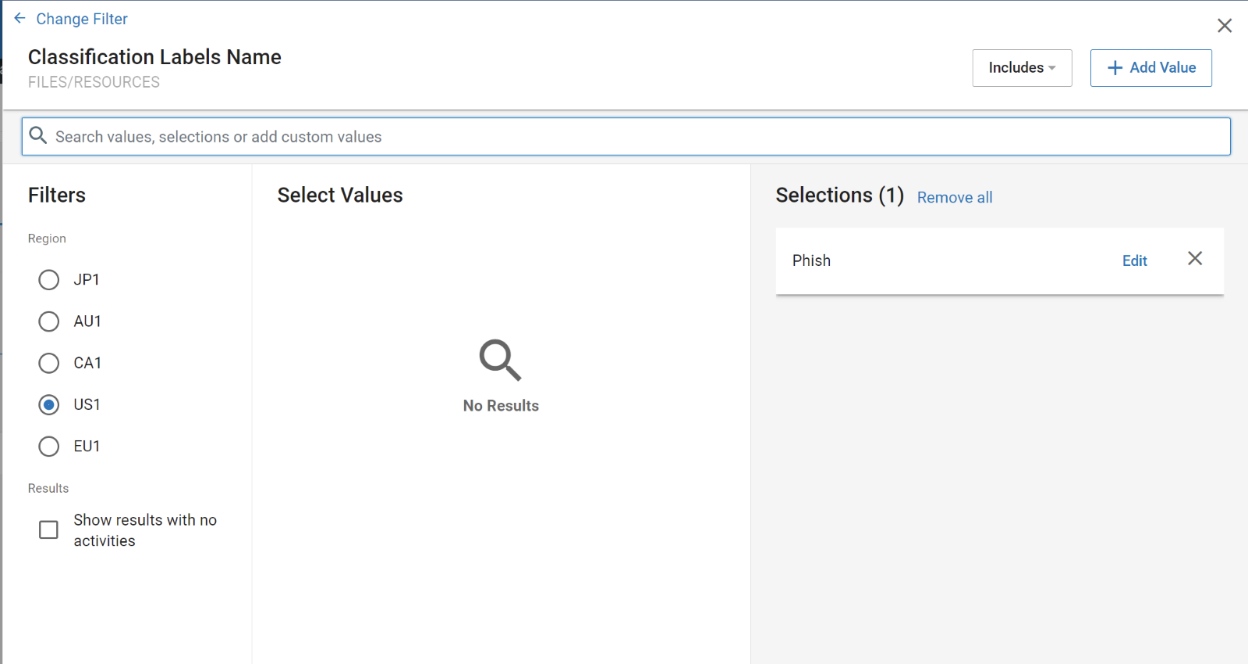
Add a new filter, then search for ‘Classification Labels Name’ in the ‘Files / Resources’ card. Select ‘Phish’.
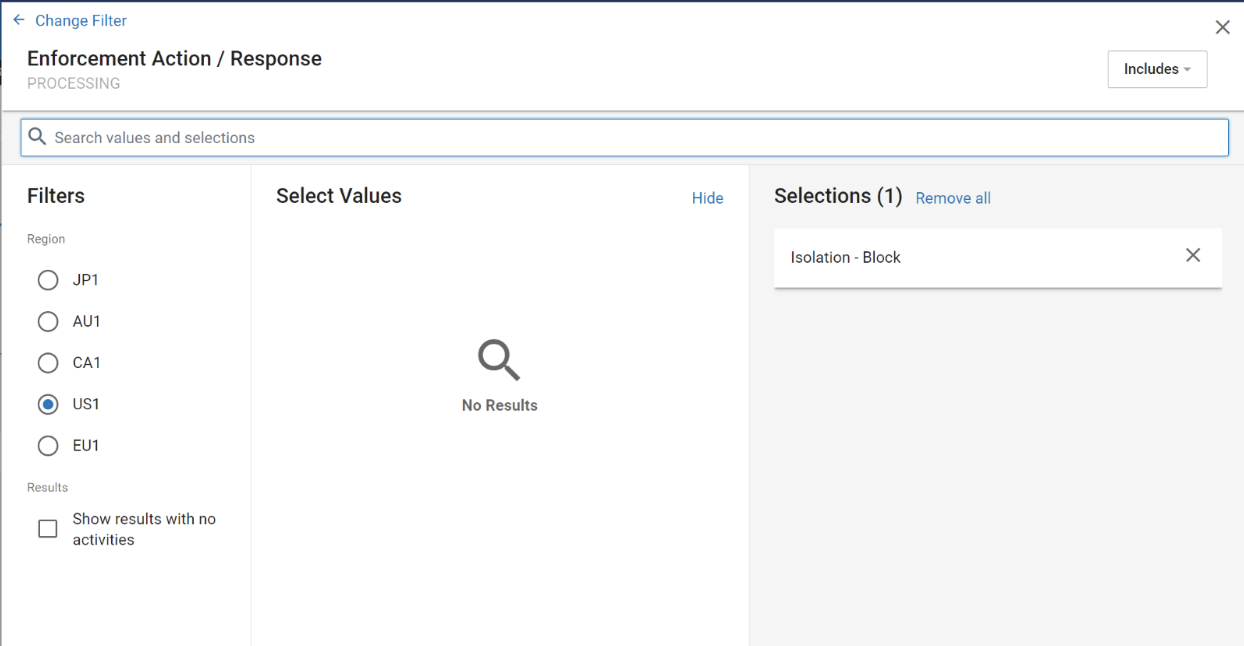
Add a new filter, then search for ‘Enforcement Action / Response’ in the ‘Processing’ card. Select ‘Isolation – Block’
Isolation Explorations and DLP Data
Isolation explorations will include sensitive data snippets that have been matches by the DLP Data Class selected in the Isolation rule corresponding to the event.