Anomaly Detection
Proofpoint anomaly detection identifies activities that deviate from the regular activities of a user. Using an algorithm that learns and trains from past behaviors, a baseline and threshold is established.
The threshold is automatically configured, no configuration is required. An anomaly alert is generated when the activity volume exceeds the threshold.
When the threshold is established and defined, major deviations are captured and an anomaly event is generated. The computed threshold allows some tolerance to adjust for minor variations from the baseline in order to avoid false positives.
All activities for a tenant are used to determine an observed user's normal activity pattern. This includes file events across all websites and URLs. Total file size and types of files are considered when detecting anomalies.
A common approach in anomaly detection is to use the median as the central value and then calculate the deviations from this median. Proofpoint takes into consideration 2 medians to identify deviation from the regular activities: user median that looks specifically at this user activity, and the tenant median that refer to the activities of all the users registered in the tenant
At least 30 days or alerts are required to compute the baseline for the anomaly threshold.
Anomaly detection is currently available with Endpoint Data and CASB Data only.
-
Endpoint detects Web File Download/Upload, USB file Copy and Print
-
Anomalous Data Access: For example, downloading a large volume of data from sanctioned sites and file sync to a specified cloud folder.
-
Anomalous Data Exfiltration: Unusual file download or upload. For example, printing, USB copy and Web file upload.
-
Anomalous Data Permission Change: Unusual changes to users. For example, file access scope changes that occur in large volumes.
-
-
CASB detects Cloud Storage Download and File Permission Change: Activity users share with their own external personal accounts. Detection helps you discover and control insider data exfiltration in the cloud by users that have left or are in the process of leaving your organization, and users who are sharing data with their own external consumer account.
Anomaly Detections Analysis
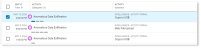
You can review and search for anomaly detections using Explorations.
When creating and Exploration:
-
Enable Source Type - Platforms Detections.
-
Filter for anomalies by selecting Activity > Primary Categories. Select the value you want:
-
Anomalous Data Access
-
Anomalous Data Exfiltration
-
Anomalous Data Permission Change
-
Forensics
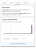
To understand why and how anomalous activity was detected, you can review the forensics in the Forensic tab.
Forensics include:
-
Description with explanation of why action was deemed an anomaly.
-
Line chart provides an at-a-glance view of typical user activity (represented by grey dots) and past anomalies (indicated by pink dots). A bar highlights the currently selected anomaly.
-
By clicking Explore Anomalous Activities, you can access further details about the activities that identified this as an anomaly, displayed in a new tab.
Detection Rules
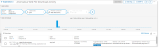
You can create detection rules to alert when an anomaly is detected.
-
From Administration application > Policies > Rules. Select New Rule and in Detection Rule, select Create Rule.
-
Name the rule.
-
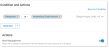
In Conditions and Actions area, Select > Select Fields.
-
In the Sources, make sure Platform Detections is enabled.
-
From the Fields, select Activity > Categories.
Select the value you want:
-
-
Anomalous Data Access
-
Anomalous Data Exfiltration
-
Anomalous Data Permission Change
-
-
-
In the Actions area, set the alerts you want.