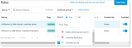
Tag Management
You can use tags to identify and categorize important information, such as activities and alerts for investigations you are working on. Tags enable faster investigations and are also useful for filtering lists and can be used in explorations and alerts. Currently, you can tag alerts, explorations, rules and conditions.
By default, Proofpoint provides you with several preconfigured tags, such as Copyright Infringement, Data Infiltration and Data Exfiltration. In addition you can create your own tags.
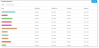
All tags can be viewed from Proofpoint Data Security & Posture in the Administration app. Select Definitions > Tags.
To see details about where a tag is used, click on it. In the example the tag is used twice in the Threat Library, twice in conditions, and once in a rule. By clicking on the arrow, you leave Tag Management and go to the relevant view.
Creating a Tag
-
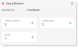
From Proofpoint Data Security & Posture, select the Administration app. Select Definitions > Tag Management.
-
Click New Tag.
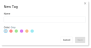
The New Tag dialog box displays.
- Give the new tag a name, select a color and click Save.
Tag Management Usage
You can use tag management throughout your work. You can apply the same tag to activities, rules, conditions, explorations and alerts to help you identify and categorize.
For example, you're creating several rules to monitor a group of employees you are watching. To make it easier to find those rules in the Rules list, you can tag each rule, in this example, watched group.
You can create the tag, from Administration, in Tag Management or you can tag the rules by selecting them from the Rules list.
-
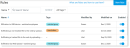
Select the rule you want to tag from the Rules list.
-
Click Add Tags.
-
Select the tag from the list or add a new tag if needed.
-
Click Done and the tag appears next to the rule in the Rules list.
-
You can then use Filter by tag to find the rules you want.
-
You can use this same tag, watched group, and tag relevant explorations, conditions and alerts.
Threat Library
By default, each item is assigned a tag. Since the Threat Library includes over 150 threat items, it is useful to filter and find the threat item you want.