To allow monitoring exfiltration of data to a shared network drive, network drives are now supported as exit points. A shared network drive is often an unsecured public drive. The shared network drive may be open to all employees regardless of employee classification or privileges.
This feature is currently available on request. Contact your Proofpoint representative.
For example, if sensitive content is copied to the shared network drive by an employee with specific privileges, any employee can now view it. This feature detects when a file is copied to a network drive, allowing you to report, alert and block the action.
File Copy to Network Drive Behavior
Any activity of file copy/move to a network drive is assigned the Primary Category or Category of Copy to Network Drive (and not File Copy).
Network Drives
Network drives include:
-
Mapped Drives: Network drive is mapped to a specific drive letter, such as N:\ or P:\
-
Unmapped Drives: Drive is not mapped to a specific drive letter and is accessed using the Universal Naming Convention (UNC) path
The destination folder on a network drive to which a file is copied/moved is displayed in these fields:
-
Files/Resources > Target Path: This shows the destination folder path as provided by the user (for example, N:\Downloads” for a mapped network drive).
Example:
-
N:\ Downloads (mapped network drive)
Target Network drive address should NOT end with a backslash (\).
Example:
-
Correct \\10.1.100.8\public\batab
-
Incorrect \\10.1.100.8\public\batab\
Example:
-
Correct: \\hq-filer02.corp.proofpoint.com\public
-
Incorrect: \\hq-filer02.corp.proofpoint.com\public\
-
-
Files/Resources > Resource URL: This shows the destination address of the target drive and folder in a universal way, showing the IP or the hostname and folder of the remote network drive, even if it’s a mapped network drive.
Examples:
-
\\10.1.100.8\Public\Downloads\
-
\\corp.local\Public\Downloads).\\corp.local\Public\Downloads).
-
-
Files/Resources > URL Domain: This show the destination drive as an IP Address or host name (without the specific folder).
Examples:
-
10.1.100.8
-
corp.local
-
Content Scanning Trigger
You can enable copy to network drive as a content scanning trigger for reporting with detection rules.
To apply content scanning, you must enable the trigger at the Agent Realm level. Agent Realm > Advanced Settings > Interaction > Scan Triggers for Detection Rules (disabled by default).
It is recommended to use this field in Detection Rules and Exploration (instead of Target Path) as it is independent of drive mapping.
Detect, Alert and Report on Exfiltration to Network Drive
You can detect, alert and report on file operation to a mapped or unmapped network drive. (Supported for Windows Explorer only.)
For Detect File Exfiltration to Network Drive to function correctly, you must enable the Windows Network Discovery option.
Using the Contains operator in Network Drive Prevention is NOT recommended.
Detecting Exfiltration to Network Drive Example
This example detects any copy activity to a network drive.
-
From the Proofpoint Information and Cloud Security Platform, select the Administration app. Select Policies > Rules > New Rule.
-
In General tab, complete the Name field and Description (optional) field.
-
In the Assignments tab, select Source Defaults you want. Click Next to continue. (See Source Defaults for Detection Rules.)
-
In the Settings tab, define the new rule using if/the logic. Start with the If area.
-
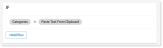
For this example, from Select, select Select Field.
-
From the Select Field list, select Activity, then select Primary Category or Categories. Select Copy to Network Drive as the value. Click Done.
This will detect any file copied to a mapped or unmapped network drive.
-
In Then area, define the alert and notification. (See Notification Policies.)
Prevent Exfiltration to Network Drive
Prevention rules are supported for File Copy to Network drive.
Actions on File Copy to a Network Drive are supported for Windows File Explorer only. When a file is copied to a network drive by non-supported method, the action is automatically allowed. This is different from other exit points where File Copy by a non-supported method (such as CMD) is automatically blocked.
Since a target path value can the IP Address or UNC, it is recommended to include both NCU and IP Address in a prevention rule, using comma separator in the Resource URL value. For example \\10.1.100.8\Public, \\hq-filer02.corp.proofpoint.com\public
This feature requires a new Prevention Rule flow. For more details about the flow, see Prevention/Endpoint Rules. Contact your Proofpoint representative for more information.
-
From the Proofpoint Information and Cloud Security Platform, select the Administration app. Select Endpoints > Prevention/EndpointRules.
-
Click New Rule and from the Prevention Rule area and click Create Rule and the Select Action to Perform panel displays.
-
In General tab, complete the Name field and Description (optional) field.
-
Click Next to continue to the Activity and Action tab.
-
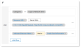
In the Activity area, select Copy to Network Drive and in the Action area, select Block or Prompt user to provide justification. Click Next.
-
In the Settings tab, in the If section, the Category is set.
-
In the Then area, select the action. Click Next.
-
From the Agent Policies, select the Agent Policies that the rule applies to. Click Save.
Allow Specific Networks
To allow copying sensitive information to a specific network or drive and block copying to all other network drives, select Category File Copy to Network drive, use the Does Not Start With operator to specify the path you want to allow copying to and specify the sensitive information.
In the example below, you want to allow users to copy credit card information only to \\hq-filer02.corp.proofpoint.com. File Copy to Network Drive blocks all networks, except a network that starts with \\hq-filer02.corp.proofpoint.com.
Exclude Specific Networks
To exclude copying sensitive information to a specific drive within the allowed network, select Category File Copy to Network drive, use the Starts With operator to specify the path you want to block copying to and specify the sensitive information.
In the example below, you want to block copying sensitive credit card information to \\hq-filer02.corp.proofpoint.com\public. Use Starts With\hq-filer02.corp.proofpoint.com\public to block this specific drive.