Classification Accounts refer to the attributes and labels applied to files with classification label solutions such as Microsoft Information Protection.
Currently this feature is available for Microsoft MIP Unified Labeling only, a cloud-based solution that lets organizations classify documents and emails by applying labels to files. From Microsoft products such as Unified Labeling client and MSFT Office, labels can be applied to files by users. This solution is available by license from Microsoft.
Azure Information Protection (AIP) labeling is also supported.
When a file enters (is downloaded to) an endpoint, the agent captures and extracts supported classification labels. Classification labels provide more context and security. The agent reads the labels and label attributes of the files, making them available in the Proofpoint Endpoint Security solution.
Extracted Labels
Labels are captured when:
-
a tracked file enters (is downloaded to) an endpoint you want to monitor by Web download
-
a tracked file is copied, moved, renamed or deleted
-
a file is exfiltrated by file upload, copying or moving it to a USB, copying or moving it to a cloud sync folder of a supported vendor
The labels extracted by the agent are for informational purposes while monitoring the file on the Proofpoint Platform. Extracted labels are based on the file's label metadata and may not be exact.
-
MIP classification labels show all the labels available in the database. This list is populated when there is file activity for a file with an MIP label.
-
For tracked files, the agent only captures MIP labels when there is file activity. If an MIP label is changed in the background, for example in MS Azure, and there is no file activity, the label will not be updated in the database.
-
If MS Office is not installed on the endpoint, the agent may not be able to extract the MIP labels.
-
The Agent extracts sub-labels. For MIP, the agent extracts the lowest sub-level, so the child label, not the parent label is extracted. For AIP, because the metadata of parent label is added to the file itself, the agent is able to extract it as well.
-
Label name and label display name may differ. The agent extracts the label name, and not the display name. (You can check the name in the Microsoft 365 Security Console > Sensitivity Labels ). The child label name is unique even if the display name is not.
-
The Agent captures Microsoft’s label name and not the display name. In Microsoft MIP, as an admin you can change only the display, the label name remains the same. The agent captures the label name even if the display name has been changed.
-
With Azure Information Protection (AIP), the Agent can extract labels and sub labels, because of the metadata on file for files labels coming from AIP.
The agent captures Microsoft’s Label Name and not the Display Name from the file's metadata. In Microsoft MIP, as an administrator you can change only the Display Name, the Label Name will remain the same in the file's metadata. In some cases, the Label GUID is shown as the Label Name and not the Display Name because the agent captured the Label Name only. (You can check the display name associated with the label name/GUID in the Microsoft 365 Security Console > Sensitivity Labels )
This feature is supported for Windows and Mac agents.
Classification labels must be enabled for an Agent Realm. By default, this setting is off. You can turn the setting on/off from the Microsoft Information Protection (MIP) Enabled option in the Advanced Settings.
Classification Accounts View
Information about the Classification is viewed from the Administration application > Integrations > Classification Accounts.
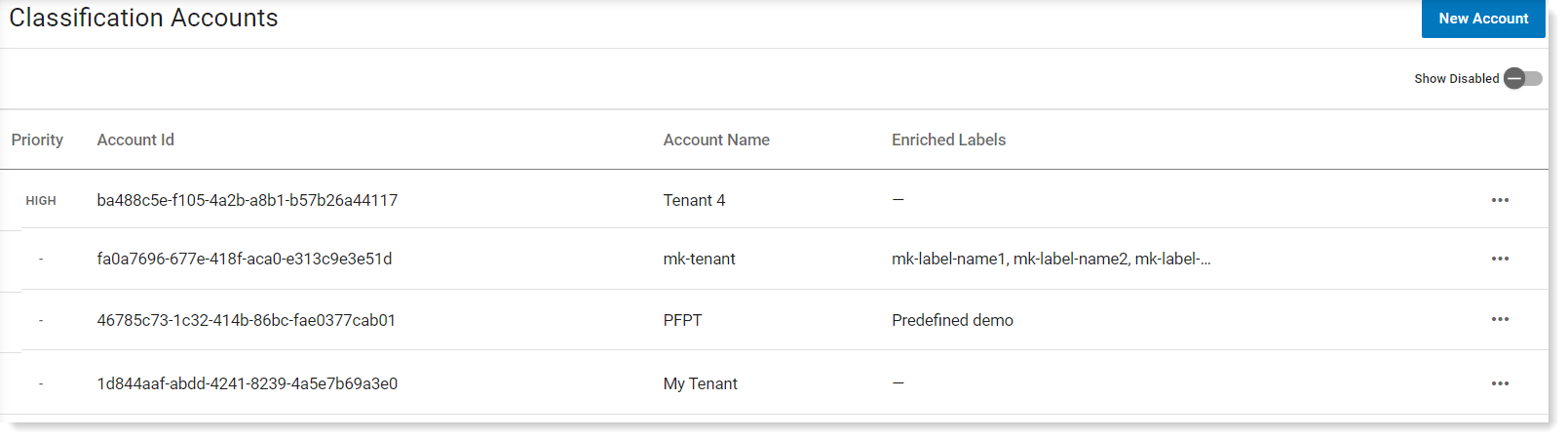
Account IDs and Account Names
-
Account ID: Tenant ID provided by Microsoft. Account IDs which are provided by classification label solutions such as in Microsoft MIP Unified Labeling, are long and difficult to identify, for example, 46785c73-1c32-414b-86bc-fae0377crpnd.
You can get the MIP account ID, from https://www.whatismytenantid.com/ or in the Microsoft Azure Portal.
-
Account Name: Name you can optionally provide. When working with classification labels, it is recommended that you provide identifiable names for your account IDs and prioritize how you want the file attributes to display when viewing them in alerts and explorations.
Enriched Labels
The agent on the endpoint extracts the Label ID and Label Name. However, if your organization has either encrypted MIP Labels or MIP Labels that were upgraded from Microsoft AIP, the Label Name may be a non-self-descriptive ID, the Label ID may not provide any information about the what it refers to.
In those cases it is recommended to manually provide a more readable Enriched Label. MIP Enriched labels let you replace the Label ID with a name that you choose. This way you can identify the MIP Label. The Enriched Label can be used for explorations, filtering and all other analytic activity.
Classification Account Priority
When a file has more than 1 account ID associated with it, the classification label associated with the account ID with the higher priority displays.
In the example, the account ID PFPT is set with the highest priority.
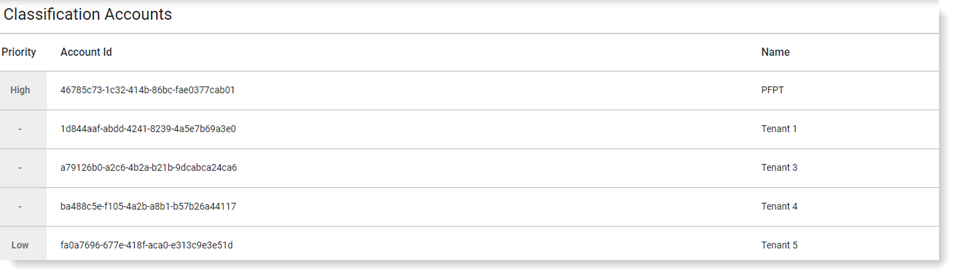
You can define what will display next to the file in the alert and exploration views. So if a file includes a classification label from the PFPT account and another account, the classification label for the PFPT account will display. In the example, ITM-General + 1, indicating 2 account IDs are associated with this file and ITM-General is associated with the account ID with the higher priority.
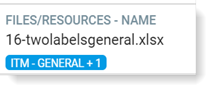
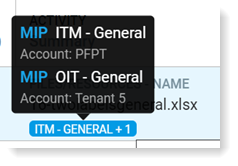
+1 indicates that another Account Id is attached to this file. The additional information is exposed in the tooltip.
Managing Classification Accounts
-
From Proofpoint Data Security & Posture, in the Administration app, Select Integrations > Classification Accounts.

-
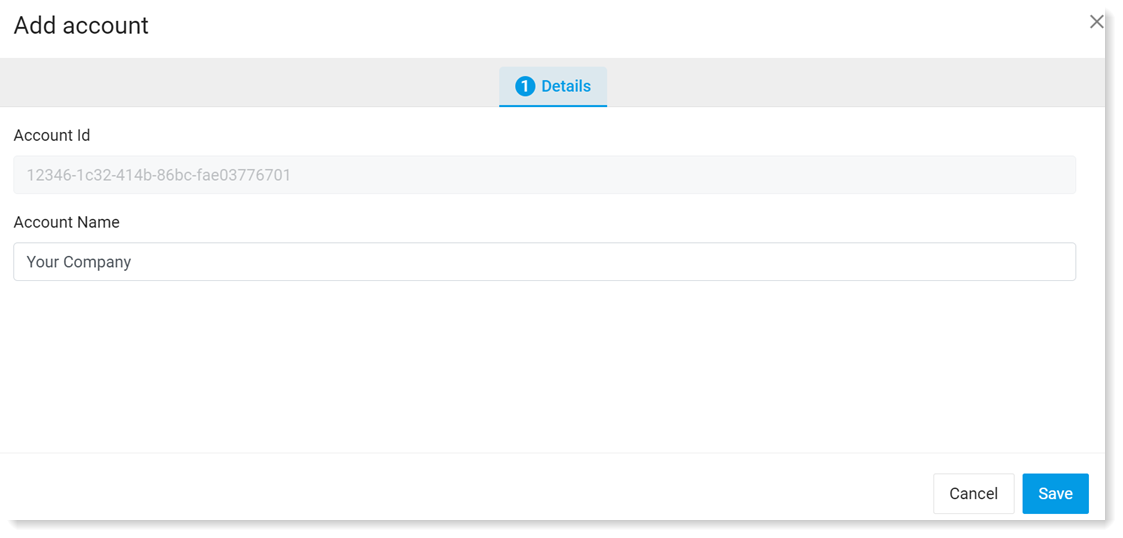
Click New Account.
-
In the Account Id field, enter the actual Office 365 tenant ID.
You can get the MIP account ID, from https://www.whatismytenantid.com/ or in the Microsoft Azure Portal.
-
In the General tab in the Account Name field, enter an identifiable name and click Next.
-
In the Label Enrichment tab, Click Add Label.
-
In the Label ID field, enter the actual Label ID and in the Label Name field, enter the descriptive name you want. Click Save.
-
You can move the account ID according to how you want to prioritize what you see.
Using Classification Labels in Data Security Workbench
You can use classification labels and their attributes when you set up explorations, rules and alerts. For example, you could set up an exploration that shows all the activity for files with a specific classification.
Classification labels are useful to set up alerts. For example, in your organization, any finance documents include the classification label finance. These files should only be used by users in the finance dept. You can set up a rule that triggers an alert whenever a document with the classification label finance is downloaded to any user not in the finance department.
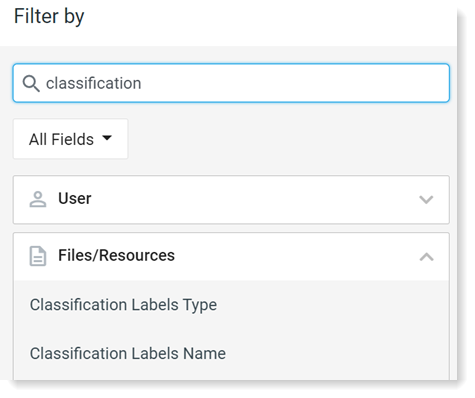
To see the classification label attributes, filter by File Resources.
-
From File Resources, select the Classification Label, field you want, for example Classification Labels Name.
If you don't see File Resources, type classification in Select Field.
You will see all the classification label names encountered by the agent.
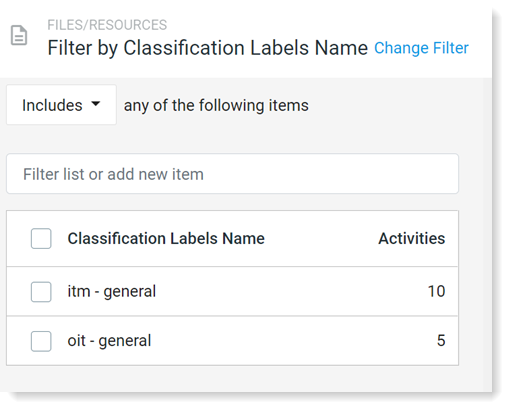
Classification Label Visibility
Classification labels and their attributes are visible in the Exploration and Alerts views, as well as in the timeline.
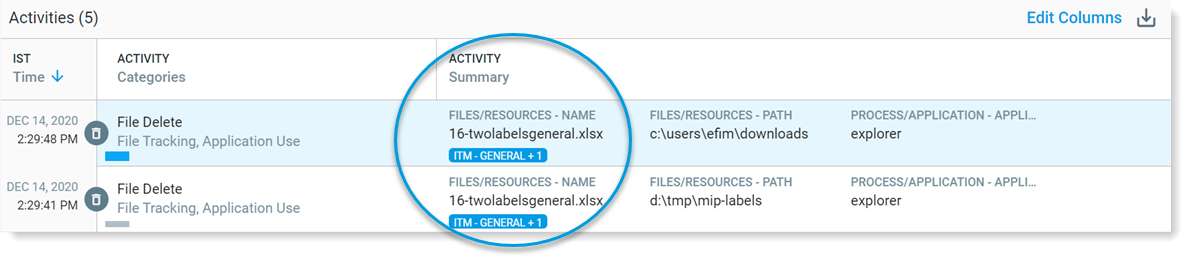
From the details area in the alert of exploration views you can see any changes to the file.
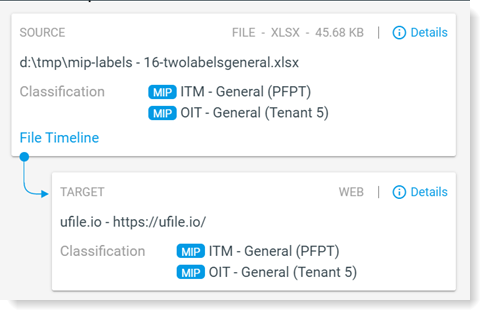
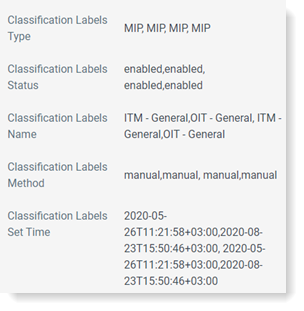
You can see the classification label attributes.
Related Topics: