File Activity Monitoring Bypass Rules let you reduce noise, false positives and improve performance. When enabled, file activity is ignored and not monitored by the Agent, reducing the load on the Agent.
This feature is available on request. Contact your Proofpoint representative.
Bypass Rules are supported for Mac Agents version 2.7.0.191. Bypass Rules are supported for Windows Agents from version 2.8.0.461.
For Windows, you can exclude file activity from specific file paths, processes or combination of both. When Bypass Rules are enabled, relevant detection and prevention rules are ignored and the bypassed activities do not display in Explorations.
For Mac, you can exclude file activity from specific processes. You can use the signature path, such as com.apple.textedit or the full binary path. Relevant prevention rules are ignored. Detection rules and Exploration file activities are not impacted.
Enabling and Adding Bypass Rules
Any rules that you want to bypass, must be added here. You can also edit and delete rules from here.
-
To enable this feature, from File Activity Monitoring settings in the Advanced Settings of the Realm, enable File Activity Monitoring Bypass Rules.
-
To add or edit rules, when enabled, from File Activity Monitoring Bypass Rules, click (Edit) Rules.
If you already have added Bypass Rules, the number of Rules displays, for example
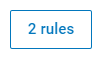 .
. -
To add a Rule, click Add Values and from the dropdown select the operating system you want (Windows or Mac).
-
For Windows, see Adding Bypass Rules for Windows.
-
For Mac, see Adding Bypass Rules for Mac.
-
-
Click Add when finished. The list of rules displays.
-
Click Done.
Adding Bypass Rules for Windows
-
In the Details area, provide a name for the rule. By default the Kind is set to Exclude.
-
In the Conditions area, add the relevant processes and paths. Make sure to do the following:
-
Process name must be the full application name including the extension, for example: chrome.exe.
-
For Paths, provide the file or folder name must include the full path, for example: c:/temp\text.txt.
-
To identify a directory, use \* at the end, for example: c:temp\*
-
For a file you must include the extension, for example: c:/temp\text.txt.
-
Adding Bypass Rules for Mac
-
In the Details area, provide a name for the rule. By default the Kind is set to Exclude.
-
In the Conditions area, add the relevant processes. Make sure to do the following:
-
Select Signature for the application signing ID, for example; com.apple.chrome.
-
Select Binary for the application full path, for example: /Applications/Google Chrome.app/contents/macOS/google or /Applications/Google Chrome.app/.
-
For recursive use /* at the end.(Supported for Binary only).
-
For literal * or ? signs use \ before the sign (Supported for Binary only).
File Activities Notes
This section describe file activities and apply to Windows Agents only.
Internal file activities: The defined path is ignored. For file movement related activities (such as file copy, move, etc.) the defined path is ignored both as source and as a destination (for example, if path ‘c:\test’ is set, it will be bypassed when a file is copies from \ to this path)
File movement to exfiltration points, the behavior is as follows:
-
File activity movements to Cloud Sync Folder: The defined path is ignored both as a source and as a destination.
-
File activity movements to USB: The destination path (on the external device) should be set to bypass the activity. Source path is currently not supported and will not bypass file movements to USB.
File activity movements to Web Upload & Print will not be ignored.
Setting a process only for Windows machines currently does not work. You must set a combination of a process and path.
-
FAM Bypass Exclude for USB Image Software
USB imaging software (such as Rufus) creates additional paths during the imaging process. To ensure the bypass rule functions correctly, you may need to add exclusions for these paths.
Do the following to identify additional paths:
-
Simulate the exclusion scenario.
-
Locate the famsc-xxxx-xx-xx.log file in the client's Logs folder.
-
Look for entries starting with FilePath that include:
-
Rule type FAMBlockAccessOnMatch
-
The desired process name in FullProcessPath
The FilePath field should indicate the actual blocked path, which needs to be added to the bypass rule.
-
Recommended BYPASS rule to apply includes both Process and the identified FilePath Path.